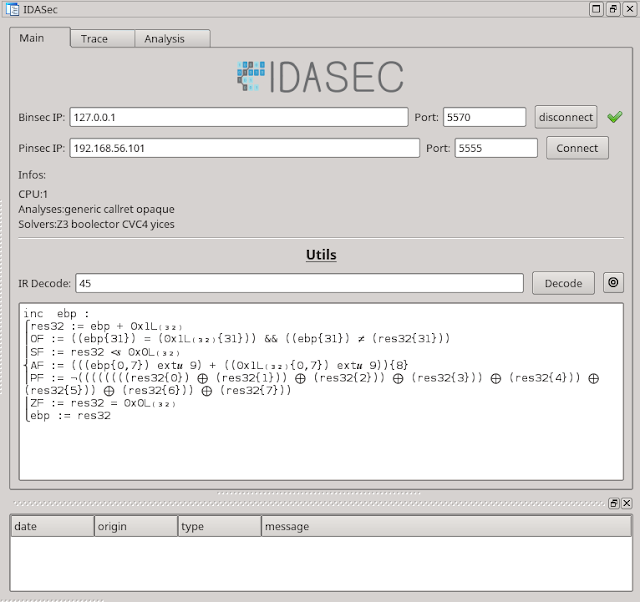
IDA plugin for reverse-engineering and dynamic interactions with the Binsec platform
Features
- Decoding an instruction (in DBA IR)
- Loading execution traces generated by Pinsec
- Triggering analyzes on Binsec and retrieving results
Dependencies
- protobuf
- ZMQ
- capstone (for trace disassembly)
- graphviz (to draw dependency within a formula)
- pyparsing
- enum
- path.py
- plotly (optional)
Running Idasec
- In IDA: Copy the
idasecfolder in the python directory of IDA and then loadidasec.pywith Ctrl+F7 - As a standalone app, just run
./idasec.py(no yet ready)
Screenshots