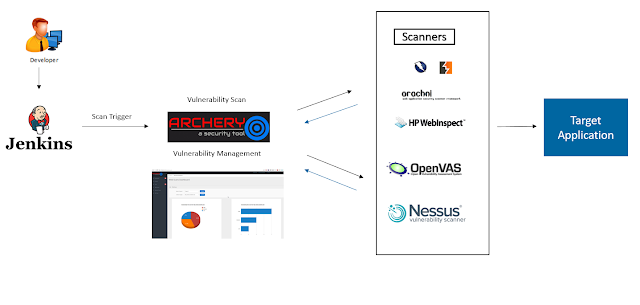
Archery is an opensource vulnerability assessment and management tool which helps developers and pentesters to perform scans and manage vulnerabilities. Archery uses popular opensource tools to perform comprehensive scanning for web application and network. It also performs web application dynamic authenticated scanning and covers the whole applications by using selenium. The developers can also utilize the tool for implementation of their DevOps CI/CD environment.
Documentation
Demo
Overview of the tool:
- Perform Web and Network vulnerability Scanning using opensource tools.
- Correlates and Collaborate all raw scans data, show them in a consolidated manner.
- Perform authenticated web scanning.
- Perform web application scanning using selenium.
- Vulnerability Management.
- Enable REST API's for developers to perform scanning and Vulnerability Management.
- Useful for DevOps teams for Vulnerability Management.
Note
Currently project is in development phase and still lot of work going on.
Requirement
- Python 2.7
- OpenVas 8
- OWASP ZAP 2.7.0
- Selenium Python Firefox Web driver
Burp Scanner
Follow the instruction in order to enable Burp REST API. You can manage and trigger scans using Archery once REST API enabled.
Installation
$ git clone https://github.com/archerysec/archerysec.git
$ cd archerysec
$ pip install -r requirements.txt
$ python manage.py collectstatic
$ python manage.py makemigrations networkscanners
$ python manage.py makemigrations webscanners
$ python manage.py makemigrations projects
$ python manage.py makemigrations APIScan
$ python manage.py makemigrations osintscan
$ python manage.py makemigrations jiraticketing
$ python manage.py migrate
$ python manage.py createsuperuser
$ python manage.py runserverDocker Installation
ArcherySec Docker is available from ArcherySec Docker
$ docker pull archerysec/archerysec
$ docker run -it -p 8000:8000 archerysec/archerysec:latest
# For persistence
docker run -it -p 8000:8000 -v <your_local_dir>:/root/.archerysec archerysec/archerysec:latest
Setup Setting
ZAP running daemon mode
Windows :
zap.bat -daemon -host 0.0.0.0 -port 8080 -config api.disablekey=true -config api.addrs.addr.name=.* -config api.addrs.addr.regex=truezap.sh -daemon -host 0.0.0.0 -port 8080 -config api.disablekey=true -config api.addrs.addr.name=.* -config api.addrs.addr.regex=trueZap Setting
- Go to Setting Page
- Edit ZAP setting or navigate URL : http://host:port/setting_edit/
- Fill below required information.
Zap API Key : Leave blank if you using ZAP as daemonapi.disablekey=true
Zap API Host : Your zap API host ip or system IP Ex.127.0.0.1or192.168.0.2
Zap API Port : ZAP running port Ex.8080
OpenVAS Setting
- Go to setting Page
- Edit OpenVAS setting or navigate URL : http://host:port/networkscanners/openvas_setting
- Fill all required information and click on save.
Road Map
- API Automated vulnerability scanning.
- Perform Reconnaissance before scanning.
- Concurrent Scans.
- Vulnerability POC pictures.
- Cloud Security scanning.
- Dashboards
- Easy to installing.
Lead Developer
Anand Tiwari - https://github.com/anandtiwarics