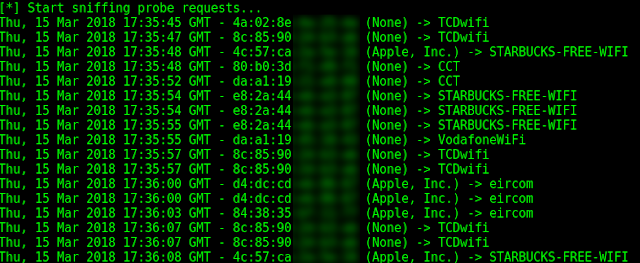
Toolkit allowing to sniff and display the Wi-Fi probe requests passing near your wireless interface.
Probe requests are sent by a station to elicit information about access points, in particular to determine if an access point is present or not in the nearby environment. Some devices (mostly smartphones and tablets) use these requests to determine if one of the networks they have previously been connected to is in range, leaking personal information.
Further details are discussed in this paper.Installation
pip3 install --upgrade probequestDocumentation
The project is documented here.
Usage
Enabling the monitor mode
To be able to sniff the probe requests, your Wi-Fi network interface must be set to monitor mode.
Command line arguments
Toolkit for Playing with Wi-Fi Probe Requests
usage:probequest[-h][--debug]-iINTERFACE[--ignore-case]
[--mode{RAW,TUI}][-oOUTPUT][--version]
[-eESSID[ESSID...]|-rREGEX]
[--excludeEXCLUDE[EXCLUDE...]|-sSTATION[STATION...]]
Named Arguments
| --debug | debug mode Default: False |
| -i, --interface | |
| wireless interface to use (must be in monitor mode) | |
| --ignore-case | ignore case distinctions in the regex pattern (default: false) Default: False |
| --mode | Possible choices: RAW, TUI set the mode to useDefault: RAW |
| -o, --output | output file to save the captured data (CSV format) |
| --version | show program’s version number and exit |
| -e, --essid | ESSID of the APs to filter (space-separated list) |
| -r, --regex | regex to filter the ESSIDs |
| --exclude | MAC addresses of the stations to exclude (space-separated list) |
| -s, --station | MAC addresses of the stations to filter (space-separated list) |