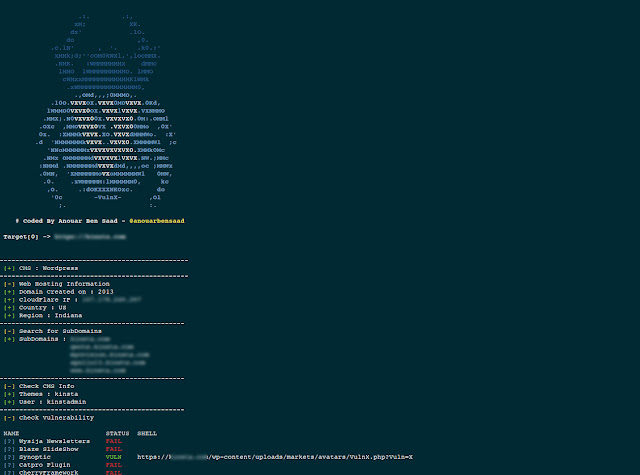
Vulnx is a cms and vulnerabilites detection, an intelligent auto shell injector, fast cms detection of target and fast scanner and informations gathering like subdomains, ipaddresses, country, org, timezone, region, ans and more ...
Instead of injecting shell and checking it works like all the other tools do, vulnx analyses the response with and recieve if shell success uploaded or no. vulnx is searching for urls with dorks.
Features
- Detect cms (wordpress, joomla, prestashop, drupal, opencart, magento, lokomedia)
- Target informations gatherings
- Target Subdomains gathering
- Multi-threading on demand
- Checks for vulnerabilites
- Auto shell injector
- Exploit dork searcher
Exploits
Joomla
- Com Jce
- Com Jwallpapers
- Com Jdownloads
- Com Weblinks
- Com Fabrik
- Com Jdownloads Index
- Com Foxcontact
- Com Blog
- Com Users
- Com Ads Manager
- Com Sexycontactform
- Com Media
- Mod_simplefileupload
- Com Facileforms
Wordpress
- Simple Ads Manager
- InBoundio Marketing
- WPshop eCommerce
- Synoptic
- Showbiz Pro
- Job Manager
- Formcraft
- PowerZoom
- Download Manager
- CherryFramework
- Catpro
- Blaze SlideShow
- Wysija-Newsletters
Drupal
- Add Admin
- Drupal BruteForcer
- Drupal Geddon2
PrestaShop
- attributewizardpro
- columnadverts
- soopamobile
- pk_flexmenu
- pk_vertflexmenu
- nvn_export_orders
- megamenu
- tdpsthemeoptionpanel
- psmodthemeoptionpanel
- masseditproduct
- blocktestimonial
- soopabanners
- Vtermslideshow
- simpleslideshow
- productpageadverts
- homepageadvertise
- homepageadvertise2
- jro_homepageadvertise
- advancedslider
- cartabandonmentpro
- cartabandonmentproOld
- videostab
- wg24themeadministration
- fieldvmegamenu
- wdoptionpanel
Opencart
- Opencart BruteForce
Available command line options
READ VULNX WIKIusage: vulnx [options]
-u --url url target to scan
-D --dorks search webs with dorks
-o --output specify output directory
-t --timeout http requests timeout
-c --cms-info search cms info[themes,plugins,user,version..]
-e --exploit searching vulnerability& run exploits
-w --web-info web informations gathering
-d --domain-info subdomains informations gathering
-l, --dork-list list names of dorks exploits
--threads number of threadsDocker
VulnX can be launched in docker.
$ git clone https://github.com/anouarbensaad/VulnX.git
$ cd VulnX
$ docker build -t vulnx ./docker/
$ docker run -it --name vulnx vulnx:latest -u http://exemple.com$ docker run -it --name vulnx -v "$PWD/logs:/VulnX/logs" vulnx:latest -u http://exemple.comInstall VulnX
$ git clone https://github.com/anouarbensaad/VulnX.git
$ cd VulnX
$ chmod + x install.sh
$ ./install.shvulnxexample command with options : settimeout=3 , cms-gathering = all , -d subdomains-gathering , run --exploits
vulnx -u http://example.com --timeout 3 -c all -d -w --exploitexample command for searching dorks : -D or --dorks , -l --list-dorks
vulnx --list-dorks return table of exploits name. vulnx -D blaze return urls found with blaze dorkVulnX Wiki • How To Use • Compatibility