Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security and post exploitation during Penetraion Tests. The scripts are written on the basis of requirement by the author during real Penetration Tests.
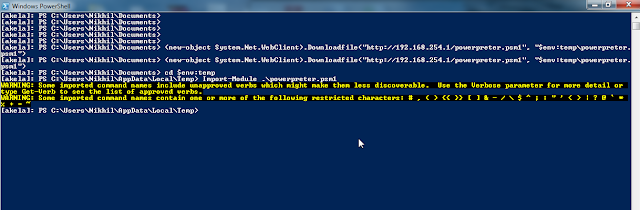
Powerpreter is a powershell module. I decided to make it a part of Nishang as there is a large amount of repeated code. This post assumes that we have Administrative access to a Windows 7 machine.
Powerpreter can surely be used as a non-admin user but obviously with limited (but still useful functionalities. Like other scripts in Nishang, I have tried my best to keep powerpreter compatible to powershellv2 so you may see some code which could be done by a cmdlet in powershellv3 and v4.
Changelog
- Added Powerpreter
- Added Execute-DNSTXT-Code
- Bug fix in Create-MultipleSessions.
- Changes to StringToBase64. It now supports Unicode encoding which makes it usable with -Encodedcommand.
- More Changes to StringToBase64. Now a file can be converted.
- Added Copy-VSS
- Information_Gather shows output in better format now.
- Information_Gather renamed to Get-Information.
- Wait for command renamed to HTTP-Backdoor.
- Time_Execution renamed Execute-OnTime
- Invoke-PingSweep renamed to Port-Scan
- Invoke-Medusa renamed to Brute-Force