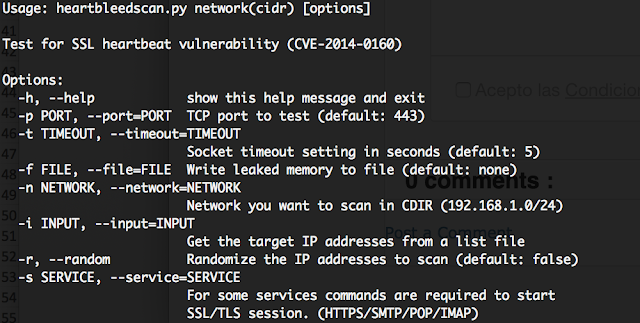
Heartbleed Vulnerability Scanner is a multiprotocol (HTTP, IMAP, SMTP, POP) CVE-2014-0160 scanning and automatic exploitation tool written with python.
For scanning wide ranges automatically, you can provide a network range in CIDR notation and an output file to dump the memory of vulnerable system to check after.
Hearbleed Vulnerability Scanner can also get targets from a list file. This is useful if you already have a list of systems using SSL services such as HTTPS, POP3S, SMTPS or IMAPS.
git clone https://github.com/hybridus/heartbleedscanner.gitSample usage
To scan your local 192.168.1.0/24 network for heartbleed vulnerability (https/443) and save the leaks into a file:
python heartbleedscan.py -n 192.168.1.0/24 -f localscan.txt -rTo scan the same network against SMTP Over SSL/TLS and randomize the IP addresses
python heartbleedscan.py -n 192.168.1.0/24 -p 25 -s SMTP -rIf you already have a target list which you created by using nmap/zmap
python heartbleedscan.py -i targetlist.txtDependencies
Before using Heartbleed Vulnerability Scanner, you should install python-netaddr package.
CentOS or CentOS-like systems :
yum install python-netaddrUbuntu or Debian-like systems :
apt-get insall python-netaddr