Faraday introduces a new concept - IPE (Integrated Penetration-Test Environment) a multiuser Penetration test IDE. Designed for distribution, indexation and analysis of the generated data during the process of a security audit.
This version comes with major changes to our Web UI, including the possibility to mark vulnerabilities as false positives. If you have a Pro or Corp license you can now create an Executive Report using only confirmed vulnerabilities, saving you even more time.
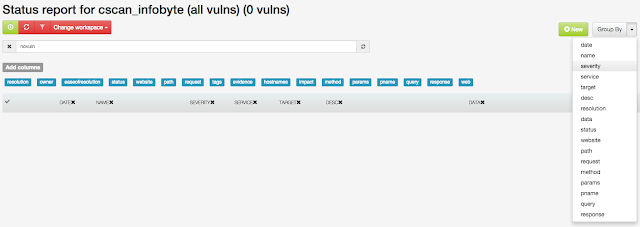
A brand new feature that comes with v1.0.16 is the ability to group vulnerabilities by any field in our Status Report view. Combine it with bulk edit to manage your findings faster than ever!
This release also features several new features developed entirely by our community.
Changes:
* Added group vulnerabilities by any field in our Status Report
* Added port to Service type target in new vuln modal
* Filter false-positives in Dashboard, Status Report and Executive Report (Pro&Corp)
 | |
| Filter in Status Report view |
* Added parametrization for port configuration on APIs
* Added scripts to:
- get all IPs from targets that have no services (/bin/getAllIpsNotServices.py)
 |
| /bin/getAllIpsNotServices.py |
It's important to note that both these scripts hold a variable that you can modify to alter its behaviour. /bin/getAllbySrv.py has a port variable set to 8080 by default. /bin/delAllVulnsWith.py does the same with a RegExp
* Added three Plugins:
- Immunity Canvas
 |
| Canvas configuration |
- Dig
- Traceroute
* Refactor Plugin Base to update active WS name in var
* Refactor Plugins to use current WS in temp filename under $HOME/.faraday/data. Affected Plugins:
- amap
- dnsmap
- nmap
- sslcheck
- wcscan
- webfuzzer
- nikto
Bug fixes:
* When the last workspace was null Faraday wouldn't start
* CSV export/import in QT
* Fixed bug that prevented the use of "reports" and "cwe" strings in Workspace names
* Unicode support in Nexpose-full Plugin
* Fixed bug get_installed_distributions from handler exceptions
* Fixed bug in first run of Faraday with log path and API errors