LeakVM: Run security tests instantly.
Why LeakVM:
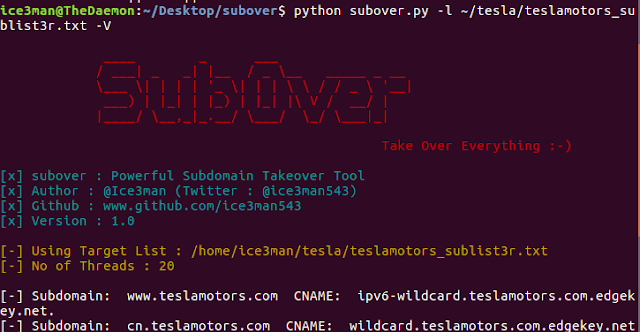
LeakVM fast security test on Android, by skipping the time-consuming build pen-testing laboratories, you can test on real devices or virtual devices. LeakVM makes researchers and pen-testers more productive since they can run the test on real time and with zero knowledge on malware develop or attacks.
Our technology uses the same techniques used in criminal software, but in a controlled environment, you always have control over the SDK, our product, gives you a real approach against real malware and real attacks.
Why Pentesting:
With 2000 million active devices, 90% of mobile users are vulnerable to exploit kits (software vulnerabilities), Cyber crime damage costs to hit $6 trillion annually by 2021, Mobile Malware Shows Rapid Growth in Volume and Sophistication, Mobile security is a big data problem.
Unsecured devices and apps are the norm, In 2017 every 4.2 seconds a new malware specimen emerges, You need to reduce the threat surface.
Rewards:
Our platform is designed even so that anyone can make money with us, without any type of investment, by sharing your reseller link, the customer that is obtained will bring you rewards, now we have 3 methods of payment: Western Union, Wire Transfer and PayPal, These rewards will be received for life, is just share a link.
For first 100 customers: new client 20%, renewal 10%.
For next 900 clients: new client 15%, renewal 10%.
After reaching 1000 clients: new client 10%, renewal 5%.
Questions:
I can inject ELF/APK code inside of the sandbox of any package ?
Yes, you can.
I can load external libraries ?
Yes, from Git's, Mediafire and another sources.
I can start a HTTP service ?
Yes, as synchronous and asynchronous way.
I can start a HTTP client ?
Yes, we have one, very configurable.
I can analyze security on ELF as V.A.S ? Yes, you can.
I can bypass OOP protections ?
Yes, there not exist: 'package', 'private', 'protected' or 'final'.
I can extract private files from external packages ?
Yes, you can see and get any file.
I can hack the Keystore ?
Yes, you can.
I can trick the Context ?
Yes, you can.
I can hack the SmartLock ?
Yes, you can.
I can use reflections in simple way ?
Yes, you can.
I can see the Linux system in simple way ?
Yes, you can.
I can install it on simple way ?
Yes, just with 2 lines on the gradle.
I can develop plugins with it ?
Yes, on the same way as AAR library.
Any can use it in a simple way ?
Yes, we develop it for dummies.
Features:
- Ptrace/ASLR/Yama Bypass
- API for 3rd party projects
- Linux common features
- Dynamic library loading
- SmartLock extraction
- Private file extractor
- KeyStore extraction
- Advanced reflection
- WebServices Engine
- Privilege escalation
- Context Spoofers
- Core Observers
- Library injection
- OOP Bypass
- Extensible
- Android 4.4 to 6.0
- Architectures Arm(32/64 bits), x86(32/64 bits), MIPS(32/64 bits)
Where is JavaDoc
How configure a Virtual Device
How Install LeakVM SDK
How Connect to API
How Test Exploits
How use Common IO methods
How to Load libraries
How to Sudo& Runas
How compile a native binary (ELF)
How to run loaded code
How to Hack OOP
How to Inject code Native/VM
How build VM Code to Inject
Downloads:
LeakVM APP
LeakVM SDK 1.0.0
Web Interface:
LeakVM Console
Social Media:
LeakVM Developers Group