- A checker (site and tool) for CVE-2014-0160: https://github.com/FiloSottile/Heartbleed
- ssltest.py: Quick and dirty demonstration of CVE-2014-0160 by Jared Stafford http://pastebin.com/WmxzjkXJ
- SSL Server Test https://www.ssllabs.com/ssltest/index.html
- Metasploit Module: https://github.com/rapid7/metasploit-framework/pull/3206/files
- Nmap NSE script: Detects whether a server is vulnerable to the OpenSSL Heartbleed: https://svn.nmap.org/nmap/scripts/ssl-heartbleed.nse
- Nmap NSE script: Quick'n'Dirty OpenVAS nasl wrapper for ssl_heartbleed based on ssl_cert_expiry.nas https://gist.github.com/RealRancor/10140249
- Heartbleeder: Tests your servers for OpenSSL: https://github.com/titanous/heartbleeder?files=1
- Heartbleed Attack POC and Mass Scanner: https://bitbucket.org/fb1h2s/cve-2014-0160
- Heartbleed Honeypot Script: http://packetstormsecurity.com/files/126068/hb_honeypot.pl.txt
↧
Collection of Heartbleed Tools (OpenSSL CVE-2014-0160)
↧
OWASP ZAP 2.3.0.1 - An easy to use integrated penetration testing tool for finding vulnerabilities in web applications
The OWASP Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.
It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to an experienced pen testers toolbox.
Some of ZAP's functionality:
- Intercepting Proxy
- Traditional and AJAX spiders
- Automated scanner
- Passive scanner
- Forced browsing
- Fuzzer
- Dynamic SSL certificates
- Smartcard and Client Digital Certificates support
- Web sockets support
- Authentication and session support
- Powerful REST based API
- Support for a wide range of scripting languages
- Automatic updating option
- Integrated and growing marketplace of add-ons
Some of ZAP's features:
- Open source
- Cross platform
- Easy to install (just requires java 1.7)
- Completely free (no paid for 'Pro' version)
- Ease of use a priority
- Comprehensive help pages
- Fully internationalized
- Translated into a dozen languages
- Community based, with involvement actively encouraged
- Under active development by an international team of volunteers
It supports the following languages:
- English
- Arabic
- Albanian
- Brazilian Portuguese
- Chinese
- Danish
- Filipino
- French
- German
- Greek
- Indonesian
- Italian
- Japanese
- Korean
- Persian
- Polish
- Russian
- Spanish
↧
↧
FakeNet - Windows Network Simulation tool for Malware Analysis
FakeNet is a tool that aids in the dynamic analysis of malicious software. The tool simulates a network so that malware interacting with a remote host continues to run allowing the analyst to observe the malware’s network activity from within a safe environment. The goal of the project is to:
- Be easy to install and use; the tool runs on Windows and requires no 3rd party libraries
- Support the most common protocols used by malware
- Perform all activity on the local machine to avoid the need for a second virtual machine
- Provide python extensions for adding new or custom protocols
- Keep the malware running so that you can observe as much of its functionality as possible
- Have a flexible configuration, but no required configuration
The tool is in its infancy of development. We started working on the tool in January 2012 and we intend to maintain the tool and add new and useful features. If you find a bug or have a cool feature you think would improve the tool please contact us.
Features
- Supports DNS, HTTP, and SSL
- HTTP server always serves a file and tries to serve a meaningful file; if the malware request a .jpg then a properly formatted .jpg is served, etc. The files being served are user configurable.
- Ability to redirect all traffic to the localhost, including traffic destined for a hard-coded IP address.
- Python extensions, including a sample extension that implements SMTP and SMTP over SSL.
- Built in ability to create a capture file (.pcap) for packets on localhost.
- Dummy listener that will listen for traffic on any port, auto-detect and decrypt SSL traffic and display the content to the console.
Demo Video
Click here to watch a demo of version 0.9 of the tool in action.
How it works
FakeNet uses a variety of Windows and third party libraries. It uses a custom HTTP and DNS server to respond to those request. It uses OpenSSL to wrap any connection with SSL. It uses a Winsock Layered Service Provider (LSP) to redirect traffic to the localhost and to listen for traffic on new ports. It uses python 2.7 for the python extensions. And, it creates the .pcap file by reconstructing a packet header based on the traffic from send/recv calls.
↧
HULK - Web Server DoS Tool
HULK is a web server denial of service tool (DDoS Tool) written for research purposes. It is designed to generate volumes of unique and obfuscated traffic at a webserver, bypassing caching engines and therefore hitting the server's direct resource pool.
The Hulk Web server is a brainchild of Barry Shteiman. This DDoS attack tool distinguishes itself from many of the other tools out in the wild. According to its creator, the Hulk Web server was born of his conclusion that most available DDoS attack tools produced predictable repeated patterns that could easily be mitigated. The principle behind the Hulk Web server is that a unique pattern is generated at each and every request, with the intention of increasing the load on the servers as well as evading any intrusion detection and prevention systems.
Some Techniques
- Obfuscation of Source Client – this is done by using a list of known User Agents, and for every request that is constructed, the User Agent is a random value out of the known list
- Reference Forgery – the referer that points at the request is obfuscated and points into either the host itself or some major prelisted websites.
- Stickiness – using some standard Http command to try and ask the server to maintain open connections by using Keep-Alive with variable time window
- no-cache – this is a given, but by asking the HTTP server for no-cache , a server that is not behind a dedicated caching service will present a unique page.
- Unique Transformation of URL – to eliminate caching and other optimization tools, I crafted custom parameter names and values and they are randomized and attached to each request, rendering it to be Unique, causing the server to process the response on each event.
↧
Kvasir - Penetration Testing Data Management Tool
Penetration Testing Data Management can be a nightmware, because well you generate a LOT of data and some information when conducing a penetration test, especially using tools – they return lots of actual and potential vulnerabilitites to review. Port scanners can return thousands of ports for just a few hosts. How easy is it to share all this data with your co-workers?
Features
That’s what Kvasir is here to help you with. Here’s what you’ll need to get started:
- The latest version of web2py
- A database (PostgreSQL known to work)
- A network vulnerability scanner (Nexpose/Nmap supported)
- Additional python libraries
- Kvasir is a web2py application and can be installed for each customer or task.
Tools Supported
At current release, Kvasir directly supports the following tools:
- Rapid7 Nexpose Vulnerability Scanner
- Nmap Security Scanner
- Metasploit Pro (limited support for Express/Framework data)
- ShodanHQ
- ImmunitySec CANVAS
- THC-Hydra
- Foofus Medusa
- John The Ripper
This design keeps data separated and from you accidentally attacking or reviewing other customers.
This tool was developed primarily for the Cisco Systems Advanced Services Security Posture Assessment (SPA) team. While not every method used by the SPA team may directly relate we hope that this tool is something that can be molded and adapted to fit almost any working scenario.
↧
↧
Hidden File Finder v3.0 - Free Tool to Find and Unhide/Remove all the Hidden Files
Hidden File Finder is the free software to quickly scan and discover all the Hidden files on your Windows system.
It performs swift multi threaded scan of all the folders parallely and quickly uncovers all the hidden files. It automatically detects the Hidden Executable Files (EXE, DLL, COM etc) and shows them in red color for easier identification. Similarly 'Hidden Files' are shown in black color and 'Hiddden Folders' are shown in blue color.
One of its main feature is the Unhide Operation. You can select one or all of the discovered Hidden files and Unhide them with just a click. Successful 'Unhide operations' are shown in green background color while failed ones are shown in yellow background.
New version v2.0 features Settings dialog to fine tune the scanning operation. Also added right click context menu to quickly perform tasks such as Unhide, Delete, Open, Scan Online using Google Search/VirusTotal etc.
It is very easy for any user with its cool GUI interface. Particularly, more useful for Penetration testers and Forensic investigators.
It works on both 32-bit & 64-bit platforms starting from Windows XP to Windows 8.
Features
- Free, Easy to use GUI based Software
- Fast multi threaded Hidden File finder to quickly scan entire computer, drive or folder.
- Unhide all the Hidden files with one click.
- Delete the selected file/folder completely
- Scan Online feature to online threat verification (mainly Executable files) using Google Search or VirusTotal.
- Right Click Context Menu to perform quick tasks.
- Settings dialog to fine tune the scanning operation.
- Color based representation of Hidden Files/Folders/Executable Files and Unhide operations.
- Sort feature to arrange the Hidden files based on name/size/type/date/path
- Detailed hidden file scan report in HTML format
- Fully portable and can be run from anywhere
- Also includes Installer for local installation/un-installation
↧
RouterPassView v1.53 - Recover lost password from router backup file
Most modern routers allow you to backup the configuration of the router into a file, and then restore the configuration from the file when it's needed.
The backup file of the router usually contains important data like your ISP user name/password, the login password of the router, and wireless network keys.
If you lost one of these password/keys, but you still have a backup file of your router configuration, RouterPassView might help you to recover your lost password from your router file.
Supported Routers
Due to large amount of router models available in the market, it's impossible to support all of them.
For now, RouterPassView supports a limited number of router models, and I'll gradually add support for more routers in future versions. Also, be aware that even if your router is not in the list, you can still try to open your router backup file with RouterPassView, because some routers are sold with different brand name, but they still use the same software/chipset of other routers.
Here's the list:
- Linksys WRT54GL (With original firmware or Tomato firmware), WRT54G (only some of them), WRT160N, WRT320N, and possibly similar models.
- Linksys E5200
- Linksys E2000
- Linksys RV082
- Linksys E2500
- Linksys N1500
- Linksys E900
- Cisco-Linksys E4200
- Edimax BR6204WG, and possibly similar models.
- Siemens ADSL SL2-141, and possibly similar models.
- Dynalink RTA1025W, and possibly similar models.
- NETGEAR WGT624, WGR614v9, WNR1000v3, WNR3500L, and possibly other models.
- ASUS WL-520g, WL-600g, and possibly similar models.
- ASUS RT-N10+ , and possibly similar models.
- Asus RT-N56U , and possibly similar models.
- Asus RT-AC66U
- D-Link DIR-655, DIR-300, and possibly similar models.
- Sanex SA 5100, and possibly similar models.
- Sitecom WL-351, WL-575, WL-312, and possibly similar models.
- COMTREND 536+ (Only Internet Login)
- US Robotics 9108 ADSL (internet login and admin login)
- D-Link DSL-2540U/BRU/D ADSL2+, DSL-2650U, DSL-520B
- D-Link DVA-G3170i/PT
- D-Link DSL-604T
- D-Link G3670B
- D-Link DSL-2640T
- D-Link DSL-G684T
- D-Link DSL-2500U
- D-Link 2740B
- D-Link DIR-615 G2
- D-Link WBR-1310
- D-Link DSL-2543B
- D-Link DI-524
- D-Link DI-624+A
- D-Link DIR-600
- D-Link DIR-300
- TL-WDR4300 N750
- TP-Link TD-8810 ADSL Modem/Router.
- Dynamode R-ADSL-C4-W-G1
- NetComm NB5Plus4 DSL
- Thomson TG580 DSL (only in Hex Dump mode)
- Asus RT-G31
- HuaWei EchoLife HG520 (Only some of them)
- HuaWei HG526
- HuaWei-3Com Aolynk BR104
- TP-LINK TL-WR841N
- TP-LINK TL-WR841DN
- TP-LINK TL-MR342
- TP-LINK TL-WR340G
- TP-LINK TL-R460
- TP-LINK TL-WR741ND v2.0
- TP-LINK TL-WR700N
- TP-LINK TL-WR740N
- TP-LINK TL-WA801N
- TP-LINK TL-WR541G
- TP-LINK TL-WR1043ND
- TP-LINK TD-W8960N
- TP-Link TL-WR941ND
- TP-Link TL-MR3220
- TP-Link TL-WR642G
- TP-Link TL-WDR3320
- TP-Link TD-W8970
- Belkin N+ (F5D8236uk4)
- Mercury MW54R
- Netgear DG632
- Netgear Wireless Cable Voice Gateway CG3000/CG3100
- Netcomm NB6W
- Aztech DSL605EW
- Comtrend CT-5072T ADSL2+ modem/router
- Small Business RV042
- Intelbras WRN240
- ipTIME N604V
- Linksys WRV200
↧
Burp Suite Professional v1.6 - The leading toolkit for web application security testing
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
Changelog v1.6
Burp Suite Free Edition contains significant new features added since v1.5, including:
- Support for WebSockets messages.
- Support for PKCS#11 client SSL certificates contained in smart cards and physical tokens.
- A new Extender tool, allowing dynamic loading and unloading of multiple extensions.
- A new powerful extensibility API, enabling extensions to customize Burp’s behavior in much more powerful ways.
- Support for extensions written in Python and Ruby.
- A new BApp Store feature, allowing quick and easy installation of extensions written by other Burp users.
- An option to resolve DNS queries over a configured SOCKS proxy, allowing access to TOR hidden services.
- Generation of CSRF PoC attacks using a new cross-domain XHR technique.
- New options for SSL configuration, to help work around common problems.
- Optional unpacking of compressed request bodies in the Proxy.
- Support for .NET DeflateStream compression.
- New and improved types of Intruder payloads.
- New Proxy interception rules.
- New Proxy match/replace rules.
- Improved layout options in the Repeater UI.
- An SSL pass-through feature, to prevent Burp from breaking the SSL tunnel for specified domains.
- Support for the Firefox Plug-n-hack extension.
- An option to copy a selected request as a curl command.
Burp Suite Professional contains a number of bugfixes and tweaks, added since the last beta version, including:
- An occasional bug causing misplaced highlights on payloads in Scanner issues has been fixed.
- A bug in which restoring default settings for the Extender tool didn’t unload any currently running extensions has been fixed.
- A display bug affecting the rendering of binary content (such as images) in the raw view of the HTTP message editor has been fixed.
- A bug which prevented the automatic backup on exit feature from functioning in headless mode has been fixed.
- In previous versions, Burp stored its preferences in separate locations for each major version. This caused persisted settings to be lost on upgrading to a new major version. This behavior has been modified, and from v1.6 onwards major versions will store their preferences in the same location. As a workaround to preserve settings from earlier releases, Pro users can launch the earlier release, save a state file containing their preferences, then launch the new release and load the state file.
↧
Simple 8-bit Assembler Simulator
↧
↧
Nmap 6.45 - Free Security Scanner For Network Exploration & Security Audits
Nmap is a utility for port scanning large networks, although it works fine for single hosts. Sometimes you need speed, other times you may need stealth. In some cases, bypassing firewalls may be required. Not to mention the fact that you may want to scan different protocols (UDP, TCP, ICMP, etc.). Nmap supports Vanilla TCP connect() scanning, TCP SYN (half open) scanning, TCP FIN, Xmas, or NULL (stealth) scanning, TCP ftp proxy (bounce attack) scanning, SYN/FIN scanning using IP fragments (bypasses some packet filters), TCP ACK and Window scanning, UDP raw ICMP port unreachable scanning, ICMP scanning (ping-sweep), TCP Ping scanning, Direct (non portmapper) RPC scanning, Remote OS Identification by TCP/IP Fingerprinting, and Reverse-ident scanning. Nmap also supports a number of performance and reliability features such as dynamic delay time calculations, packet timeout and retransmission, parallel port scanning, detection of down hosts via parallel pings.
Changes: Added ssl-heartbleed script to detect the Heartbleed bug in OpenSSL. Various other additions and updates.
↧
HonSSH - Log all SSH communications between a client and server
HonSSH is a high-interaction Honey Pot solution.
HonSSH will sit between an attacker and a honey pot, creating two separate SSH connections between them.
Features
- Captures all connection attempts to a text file.
- When an attacker sends a password guess, HonSSH can automatically replace their attempt with the correct password (spoof_login option). This allows them to login with any password but confuses them when they try to sudo with the same password.
- All interaction is captured into a TTY log (thanks to Kippo) that can be replayed using the playlog utility included from Kippo.
- A text based summary of an attackers session is captured in a text file.
- Sessions can be viewed or hijacked in real time (again thanks to Kippo) using the management telnet interface.
↧
SmartSniff - Capture TCP/IP packets on your network adapter
SmartSniff is a network monitoring utility that allows you to capture TCP/IP packets that pass through your network adapter, and view the captured data as sequence of conversations between clients and servers. You can view the TCP/IP conversations in Ascii mode (for text-based protocols, like HTTP, SMTP, POP3 and FTP.) or as hex dump. (for non-text base protocols, like DNS)
SmartSniff provides 3 methods for capturing TCP/IP packets :
- Raw Sockets (Only for Windows 2000/XP or greater): Allows you to capture TCP/IP packets on your network without installing a capture driver. This method has some limitations and problems.
- WinPcap Capture Driver: Allows you to capture TCP/IP packets on all Windows operating systems. (Windows 98/ME/NT/2000/XP/2003/Vista) In order to use it, you have to download and install WinPcap Capture Driver from this Web site. (WinPcap is a free open-source capture driver.)This method is generally the preferred way to capture TCP/IP packets with SmartSniff, and it works better than the Raw Sockets method.
- Microsoft Network Monitor Driver (Only for Windows 2000/XP/2003): Microsoft provides a free capture driver under Windows 2000/XP/2003 that can be used by SmartSniff, but this driver is not installed by default, and you have to manually install it, by using one of the following options:
- Option 1: Install it from the CD-ROM of Windows 2000/XP according to the instructions in Microsoft Web site
- Option 2 (XP Only) : Download and install the Windows XP Service Pack 2 Support Tools. One of the tools in this package is netcap.exe. When you run this tool in the first time, the Network Monitor Driver will automatically be installed on your system.
- Microsoft Network Monitor Driver 3: Microsoft provides a new version of Microsoft Network Monitor driver (3.x) that is also supported under Windows 7/Vista/2008. Starting from version 1.60, SmartSniff can use this driver to capture the network traffic.The new version of Microsoft Network Monitor (3.x) is available to download from Microsoft Web site.Notice:If WinPcap is installed on your system, and you want to use the Microsoft Network Monitor Driver method, it's recommended to run SmartSniff with /NoCapDriver, because the Microsoft Network Monitor Driver may not work properly when WinPcap is loaded too.
↧
Ninja PingU - High performance network scanner tool for large scale analyses
NINJA-PingU Is Not Just a Ping Utility is a free open-source high performance network scanner tool for large scale analyses. It has been designed with performance as its primary goal and developed as a framework to allow easy plugin creation.
NINJA PingU comes out of the box with a set of plugins for services analysis and embedded devices identification. More information about those can be found in its home page at http://owasp.github.io/NINJA-PingU
Usage:
# sudo ./bin/npingu [OPTIONS] targets
-t Number of sender threads.
-p Port scan range. For instance, 80 or 20-80.
-d Delay between packages sent (in usecs).
-s No service identification (less bandwith load, more hosts/time).
-m Module to run. For instance, Service.
-h Show this help.
[targets] Ip address seed. For instance, 192.168.1. or 1.1.1.1-255.0.0.0Examples:
Example to scan some OVH servers:
# ./bin/npingu -t 3 -p 20-80 188.1.1.1-188.255.1.1 -d 1 -m Service
-Targeted Hosts [188.165.83.148-188.255.83.148]
-Targeted Port Range [20-80]
-Threads [3]
-Delay 1 usec
-Use the Service identification ModuleExample to scan several google web servers:
# ./bin/npingu -t 5 -p 80 -s 74.125.0.0-74.125.255.255
-Targeted Hosts [74.125.0.0-74.125.255.255]
-Targeted Port [80]
-Threads [5]
-s synOnly scanExample for scanning the 32764/TCP Backdoor
# ./bin/npingu -t 2 1.1.1.1-255.1.1.1 -m Backdoor32764 -p 32764
-Targeted Hosts [1.1.1.1-255.1.1.1]
-Targeted Port [32764]
-Threads [2]
-Use the 32764/TCP Backdoor Module↧
↧
FS-NyarL - Network Takeover & Forensic Analysis Tool
NyarL it's Nyarlathotep, a mitological chaotic deity of the writer HP. Lovecraft's cosmogony.
It's represent Crawling Chaos and FS-NyarL it's The Crawling Chaos of Cyber Security :-)
A network takeover & forensic analysis tool - useful to advanced PenTest tasks & for fun and profit - but use it at your own risk!
- Interactive Console
- Real Time Passwords Found
- Real Time Hosts Enumeration
- Tuned Injections & Client Side Attacks
- ARP Poisoning & SSL Hijacking
- Automated HTTP Report Generator
ATTACKS IMPLEMENTED:
POST ATTACKS DATA OBTAINED:
- MITM (Arp Poisoning)
- Sniffing (With & Without Arp Poisoning)
- SSL Hijacking (Full SSL/TLS Control)
- HTTP Session Hijaking (Take & Use Session Cookies)
- Client Browser Takeover (with Filter Injection in data stream)
- Browser AutoPwn (with Filter Injection in data steam)
- Evil Java Applet (with Filter Injection in data stream)
- DNS Spoofing
- Port Scanning
POST ATTACKS DATA OBTAINED:
- Passwords extracted from data stream
- Pcap file with whole data stream for deep analysis
- Session flows extracted from data stream (Xplico & Chaosreader)
- Files extracted from data stream
- Hosts enumeration (IP,MAC,OS)
- URLs extracted from data stream
- Cookies extracted from data stream
- Images extracted from data stream
- List of HTTP files downloaded extracted from URLs
DEPENDENCIES (aka USED TOOLS):
- Chaosreader (already in bin folder)
- Xplico
- Ettercap
- Arpspoof
- Arp-scan
- Mitmproxy
- Nmap
- Tcpdump
- Beef
- SET
- Metasploit
- Dsniff
- Macchanger
- Hamster
- Ferret
- P0f
- Foremost
- SSLStrip
- SSLSplit
↧
KisMAC - Free Sniffer/Scanner application for Mac OS X
KisMAC is an open-source and free sniffer/scanner application for Mac OS X. It has an advantage over MacStumbler / iStumbler / NetStumbler in that it uses monitor mode and passive scanning.
KisMAC supports many third party USB devices: Intersil Prism2, Ralink rt2570, rt73, and Realtek rtl8187 chipsets. All of the internal AirPort hardware is supported for scanning.
The rest of this wiki assumes you are prepared for advanced topics and know what you are doing with your system.
Features
- Reveals hidden / cloaked / closed SSIDs
- Shows logged in clients (with MAC Addresses, IP addresses and signal strengths)
- Mapping and GPS support
- Can draw area maps of network coverage
- PCAP import and export
- Support for 802.11b/g
- Different attacks against encrypted networks
- Deauthentication attacks
- AppleScript-able
- Kismet drone support (capture from a Kismet drone)
Supported hardware chipsets
- Apple AirPort and AirPort Extreme (dependent upon Apple's drivers)
- Intersil Prism 2, 2.5, 3 USB devices
- Ralink rt2570 and rt73 USB devices
- Realtek RTL8187L USB (such as the Alfa AWUS036H, which does not work on Mac OS 10.6.7 or later)
Crypto support
- Bruteforce attacks against LEAP, WPA and WEP
- Weak scheduling attack against WEP
- Newsham 21-bit attack against WEP
↧
Pyew - A Python tool for static malware analysis
Pyew is a (command line) python tool to analyse malware. It does have support for hexadecimal viewing, disassembly (Intel 16, 32 and 64 bits), PE and ELF file formats (it performs code analysis and let you write scripts using an API to perform many types of analysis), follows direct call/jmp instructions in the interactive command line, displays function names and string data references; supports OLE2 format, PDF format and more. It also supports plugins to add more features to the tool.
Pyew have been successfully used in big malware analysis systems since almost 2 years, processing thousand of files daily.
↧
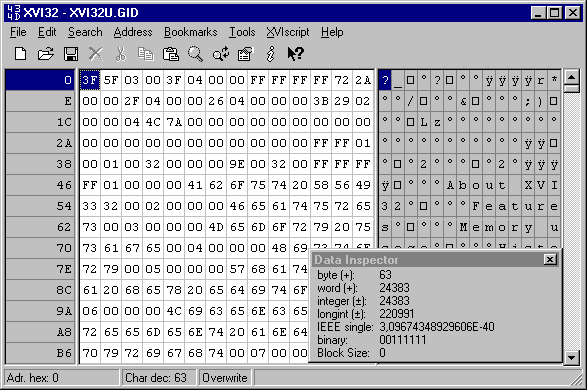
XVI32 - Freeware Hex Editor
XVI32 is a freeware hex editor running under Windows 9x/NT/2000/XP/Vista/7. The name XVI32 is derived from XVI, the roman notation for the number 16. XVI32 and all of its components are developed by myself.
The current release 2.55 is available since June 26, 2012. It comes with a complete online help and requires only 1.02 MB of hard disk space. There is no setup program needed - just unzip the downloaded archive to your hard disk! XVI32 doesn't write any data to your registry.
XVI32 is used by thousands of people all over the world. It was included in books like the Hacker's Guide. Even people at Microsoft ™ do use XVI32! If you don't believe me, look at http://support.microsoft.com/kb/835840/EN-GB/.
Features
XVI32 has the following main features. Especially note the highlighted advantages of XVI32.
- XVI32 is a portable application, i.e. no setup program is needed, you can run XVI32 from your USB stick, no data is written to the registry
- data inspector to view decoded numbers (see screen shot; can be turned off).
- Has built-in script interpreter.
- Easily works with huge files. Try to open a 60 MB sized text file with some other hex editor (not to speak about Wordpad), then use XVI32... If you don't have such a huge text file, use my freeware tool RndFile to create one
- XVI32 allows to edit files up to 2 GB (enough virtual memory provided, of course)
- For your convenience, XVI32 stores settings and last used search strings etc. in XVI32.INI file
- Progress indication in percent for most operations
- You can abort nearly all operations (reading/writing files, search, replace, print...)
- Display of both text (ASCII/ANSI) and hexadecimal representation
- Two synchronous cursors in text and hex area
- Fully resizeable window (change number of rows and columns)
- Font and font size adjustable
- Overwrite or insert characters
- Insert text or hex string n times
- Switch byte offset (address) of first byte between 0 or 1 to examine also record structure of plain text files
- Search text or hex string, e.g. find "this text" or find "0D 0A"
- Simplified search for Unicode Latin (UTF-16) strings
- Search optionally with joker (wildcard) char that will match any character, e.g. find "A.C" or "00 2E 2E 00" where "." = "2E" (user-defined) stands for any character
- Fast searching algorithm (Quicksearch) for both search directions (down/up)
- Count occurences of text or hex string
- Replace text or hex string, e.g. replace "0D 0A" by "0A" or replace "0D 0A" by text "EOL"
- Extremely fast "replace all" mode (if needed, additional memory is allocated beforehead, not at every single replacing operation)
- Menu item Shredder data to overwrite all bytes of a file with binary zeroes
- Auto-fill feature to copy bytes from current address into input field for hex string using right arrow key
- Character conversion using self-defined character table
- Easy converting of text to hex string in dialogs (e.g. "abc" -> "61 62 63")
- Decoding and encoding of 1, 2, 4, and 8 byte integers or 4/8 byte floats in 2 possible byte orders
- Bit manipulation (view or set bits)
- Open file in Read Only Mode (e.g. if opened by another application or to avoid unintentional modifications)
- Insert file contents into file
- Write block to file
- Copy, move or delete block
- Clipboard support
- Goto address (absolute or relative up/down)
- Up to 9 named bookmarks
- Enter jump width and jump up/down (useful for files with fixed record length)
- Patch BORLAND PASCAL 7.0 EXE files for execution on processors > 200 MHz
- Printing with preview or print to file
- Simplified search for Unicode Latin (UTF-16) strings
- Command "Reload" to open current file again
- Easily access most recently used files
- And last, but not least: XVI32 is free!
↧
↧
Shodan Plugin for Chrome
The Shodan plugin tells you where the website is hosted (country, city), who owns the IP and what other services/ ports are open.
The Shodan plugin for Chrome automatically checks whether Shodan has any information for the current website. Is the website also running FTP, DNS, SSH or some unusual service? With this plugin you can see all the info that Shodan has collected on a given website/ domain.
↧
Instant PDF Password Remover v3.5 - Free PDF Password & Restrictions Removal Tool
Instant PDF Password Remover is the FREE tool to instantly remove Password of protected PDF document. It can remove both User & Owner password along with all PDF file restrictions such as Copy, Printing, Screen Reader etc.
Often we receive password protected PDF documents in the form of mobile bills, bank statements or other financial reports. It is highly inconvenient to remember or type these complex and long passwords.
'Instant PDF Password Remover'helps you to quickly remove the Password from these PDF documents. Thus preventing the need to type these complex/long password every time you open such protected PDF documents.
Note that it cannot help you to remove the unknown password. It will only help you to remove the KNOWN password so that you don't have to enter the password everytime while opening the PDF file.
It makes it even easier with the 'Right Click Context Menu' integration. This allows you to simply right click on the PDF file and launch the tool. Also you can Drag & Drop PDF file directly onto the GUI window to start the password removal operation instantly.
It can unlock PDF document protected with all versions of Adobe Acrobat Reader using different (RC4, AES) encryption methods.
It comes with Installer for quick installation/un-installation. It works on wide range of Operating systems starting from Windows XP to Windows 8.
↧
Andiparos - Security tool that can be used for web application security assessments
Andiparos is a fork of the famous Paros Proxy. It is an open source web application security assessment tool that gives penetration testers the ability to spider websites, analyze content, intercept and modify requests, etc.
The advantage of Andiparos is mainly the support of Client Certificates on Smartcards. Moreover it has several small interface enhancements, making the life easier for penetration testers...
Features:
- Smartcard support
- BeanShell support
- History Filter (URLs)
- Passive Scanner
- Advanced search functionality
- MultiTags for request/response
- Mark Request/Response
- Better Mac OS X integration
- other nice enhancements...
For stability reasons, JDIC support has been completely removed.
↧