↧
NWHT - Network Wireless Hacking Tools
↧
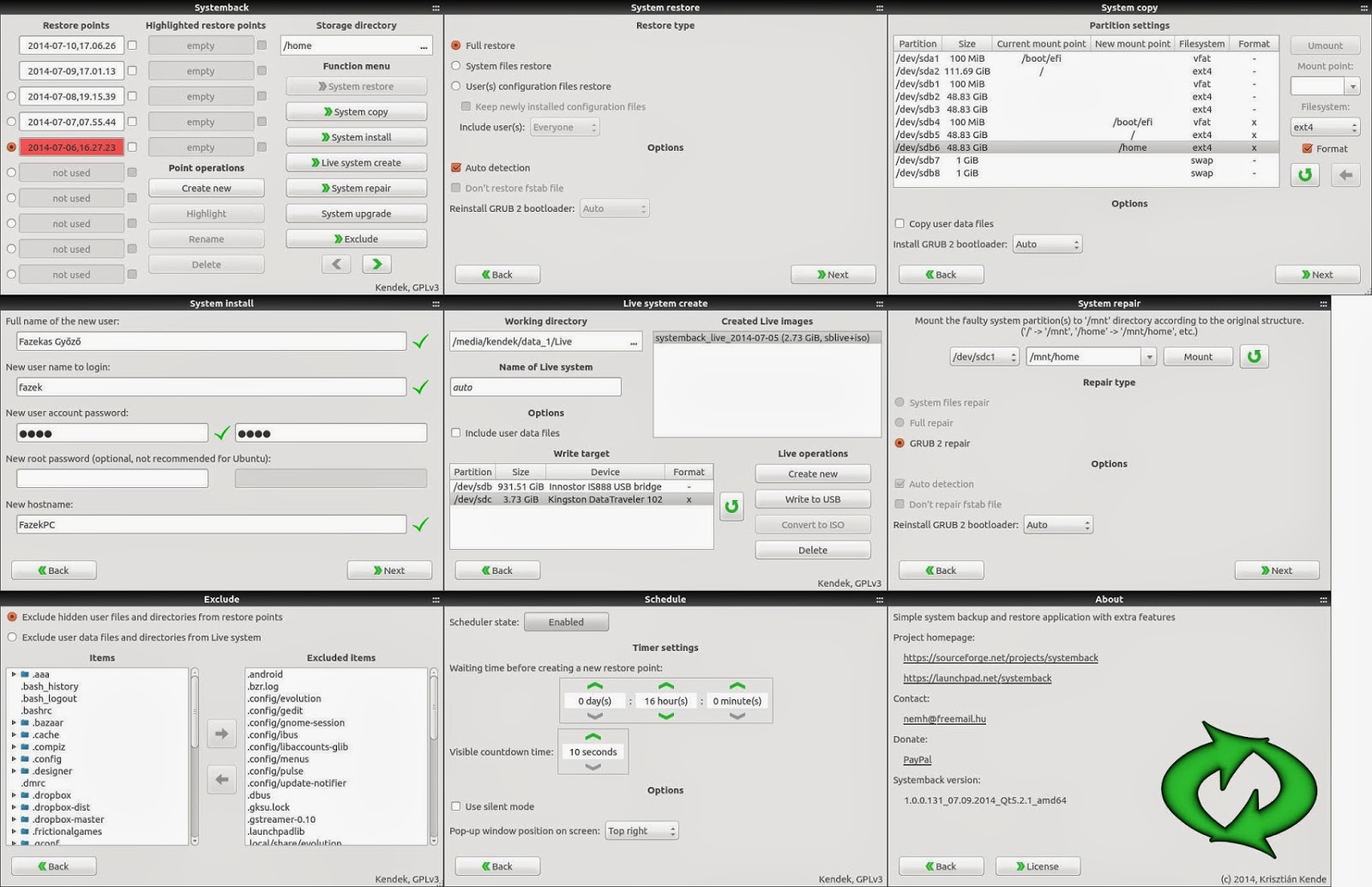
Systemback - Simple system backup and restore application with extra features
↧
↧
Dirs3arch - HTTP(S) Directory/File Brute Forcer
dirs3arch is a simple command line tool designed to brute force directories and files in websites.
Features
![]()
Features
- Keep alive connections
- Multithreaded
- Detect not found web pages when 404 not found errors are masked (.htaccess, web.config, etc).
- Recursive brute forcing
Usage: dirs3arch.py [-u|--url] target [-e|--extensions] extensions [options]
Options:
-h, --help show this help message and exit
Mandatory:
-u URL, --url=URL URL target
-e EXTENSIONS, --extensions=EXTENSIONS
Extensions list separated by comma (Example: php, asp)
Dictionary Settings:
-w WORDLIST, --wordlist=WORDLIST
-l, --lowercase
General Settings:
-r, --recursive Bruteforce recursively
-t THREADSCOUNT, --threads=THREADSCOUNT
Number of Threads
-x EXCLUDESTATUSCODES, --exclude-status=EXCLUDESTATUSCODES
Exclude status code, separated by comma (example: 301,
500)
--cookie=COOKIE, --cookie=COOKIE
--user-agent=USERAGENT, --user-agent=USERAGENT
--no-follow-redirects, --no-follow-redirects
Connection Settings:
--timeout=TIMEOUT, --timeout=TIMEOUT
Connection timeout
--ip=IP, --ip=IP Destination IP (instead of resolving domain, use this
ip)
--http-proxy=HTTPPROXY, --http-proxy=HTTPPROXY
Http Proxy (example: localhost:8080
--max-retries=MAXRETRIES, --max-retries=MAXRETRIES
Reports:
-o OUTPUTFILE, --output=OUTPUTFILE
--json-output=JSONOUTPUTFILE, --json-output=JSONOUTPUTFILE↧
Domain Analyzer Security Tool - Finds all the security information for a given domain name
Domain analyzer is a security analysis tool which automatically discovers and reports information about the given domain. Its main purpose is to analyze domains in an unattended way.
Features
- It creates a directory with all the information, including nmap output files.
- It uses colors to remark important information on the console.
- It detects some security problems like host name problems, unusual port numbers and zone transfers.
- It is heavily tested and it is very robust against DNS configuration problems.
- It uses nmap for active host detection, port scanning and version information (including nmap scripts).
- It searches for SPF records information to find new hostnames or IP addresses.
- It searches for reverse DNS names and compare them to the hostname.
- It prints out the country of every IP address.
- It creates a PDF file with results.
- It automatically detects and analyze sub-domains!
- It searches for domains emails.
- It checks the 192 most common hostnames in the DNS servers.
- It checks for Zone Transfer on every DNS server.
- It finds the reverse names of the /24 network range of every IP address.
- It finds active host using nmap complete set of techniques.
- It scan ports using nmap.
- It searches for host and port information using nmap.
- It automatically detects web servers used.
- It crawls every web server page using our Web Crawler Security Tool.
- It filters out hostnames based on their name.
- It pseudo-randomly searches N domains in google and automatically analyze them!
- Uses CTRL-C to stop current analysis stage and continue working.
↧
RunFromProcess - Run a Windows program with a user of another process
RunFromProcess is a command-line utility that allows you to run a program from another process that you choose.
The program that you run will be executed as a child of the specified process and it'll run with the same user and security context of the specified parent process.
Using RunFromProcess
RunFromProcess requires 2 command-line parameters:
RunFromProcess.exe [Parent Process Name/ID] [Process To Run]
The first parameter is the process name (for example: myprocess.exe) or process ID of the parent process that will run the program you need.
The second parameter is the full path filename of the program that you want to run. You can also specify command-line parameters for the specified program.
Optionally, you can specify 'nomsg' prefix before the 2 major parameters if you want that RunFromProcess won't display any error message.
Optionally, you can specify 'admin' prefix before all other parameters if you want to execute RunFromProcess as administrator.
Examples:
RunFromProcess.exe 761 c:\temp\myprog.exe
RunFromProcess.exe explorer.exe "c:\program files\abcd\mm.exe" 34 abc dd
RunFromProcess.exe nomsg explorer.exe "c:\software\soft.exe"
RunFromProcess.exe admin winlogon.exe "c:\software\soft.exe"
What you can do with this tool
Here's an example of what you can do with this tool:
when you run a program from the schedule service of Windows, the program will run under a SYSTEM account, for example:
at 18:00 c:\software\myprogram.exe
If you want to run the program with the current logged-on user, you can do it in this way:
at 18:00 c:\software\RunFromProcess.exe nomsg explorer.exe c:\software\myprogram.exe
If you want to run a program with SYSTEM user, you can do it in this way: (The admin parameter is needed to get admin rights on Windows Vista/7/8 when UAC is turned on)
RunFromProcess.exe admin winlogon.exe c:\windows\regedit.exe
If you execute the above command on Windows 7/Vista, RegEdit will be opened with a SYSTEM account, and you'll be able to see all secret Registry keys that are not available for any other user.
↧
↧
ProcessThreadsView - View process threads information On Windows
ProcessThreadsView is a small utility that displays extensive information about all threads of the process that you choose. The threads information includes the ThreadID, Context Switches Count, Priority, Created Time, User/Kernel Time, Number of Windows, Window Title, Start Address, and more.
When selecting a thread in the upper pane, the lower pane displays the following information: Strings found in the stack, stack modules addresses, call stack, and processor registers.
Using ProcessThreadsView
ProcessThreadsView doesn't require any installation process or additional dll files. In order to start using it, simply run the executable file - ProcessThreadsView.exe
After running ProcessThreadsView, you should choose the process that you want to inspect.
After you choose the desired process, the list of all threads is displayed on the main window and automatically refreshed on every threads change. When you select a thread on the upper pane, the lower pane displays extensive information about the selected thread, according to the options you choose under the Options menu.
By default, only 'Show Stack Strings' option is selected, but you can also choose to show the stack binary values, stack module addresses, other stack values, call stack, and processor regsiters.
Be aware that if turn on all available options, the loading process of the lower pane might be quite slow.
↧
Hash Compare - File Integrity Comparison Tool
Hash Compare is the FREE File Hash comparison tool. It performs Hash based Integrity Comparison using any of the the popular hash algorthms such as MD5, SHA1 or SHA256.
To make the task easier and quicker, it also supports the 'File Drag & Drop' feature. That means you can just drag & drop one or both files directly without wasting much time in selecting them.
Hash based method is the standard way of verifying the integrity of files. Often it is used to check the Integrity of Download Files downloaded from the internet. It is also used to compare two versions of the same file. In such cases HashCompare comes handy in performing quick comparison of the files.
It is fully portable and works on all Windows platforms starting from Windows XP to Windows 8.
- Performs File Integrity Comparison using popular Hash algorithms such as MD5, SHA1 & SHA256.
- 'Drag & Drop' feature to quickly drag one or both files.
- Save the file comparison report to HTML/TEXT/XML file
- Displays detailed status during the operation.
- Auto copy the Hash data to clipboard on successful comparison
- Simple, easy to use GUI Interface.
- Completely Portable Tool, can be run from anywhere.
↧
Viper - A binary management and analysis framework dedicated to malware and exploit researchers
Viper is a binary analysis and management framework. Its fundamental objective is to provide a solution to easily organize your collection of malware and exploit samples as well as your collection of scripts you created or found over the time to facilitate your daily research. Think of it as a Metasploit for malware researchers: it provides a terminal interface that you can use to store, search and analyze arbitraty files with and a framework to easily create plugins of any sort.
↧
Osueta - A simple Python script to exploit the OpenSSH User Enumeration Timing Attack
Osueta it's a simple Python2 script to exploit the OpenSSH User Enumeration Timing Attack, present in OpenSSH versions 5.* and 6.*. The script has the ability to make variations of the username employed in the bruteforce attack, and the possibility to establish a DOS condition in the OpenSSH server.
usage: osueta.py [-h] [-H HOST] [-k HFILE] [-f FQDN] [-p PORT] [-L UFILE]
[-U USER] [-d DELAY] [-v VARI] [-o OUTP] [-l LENGTH]
[-c VERS] [--dos DOS] [-t THREADS]
OpenSSH User Enumeration Time-Based Attack Python script
optional arguments:
-h, --help show this help message and exit
-H HOST Host Ip or CIDR netblock.
-k HFILE Host list in a file.
-f FQDN FQDN to attack.
-p PORT Host port.
-L UFILE Username list file.
-U USER Only use a single username.
-d DELAY Time delay fixed in seconds. If not, delay time is calculated.
-v VARI Make variations of the username (default yes).
-o OUTP Output file with positive results.
-l LENGTH Length of the password in characters (x1000) (default 40).
-c VERS Check or not the OpenSSH version (default yes).
--dos DOS Try to make a DOS attack (default no).
-t THREADS Threads for the DOS attack (default 5).↧
↧
Password Security Scanner - Check the security/strength of your passwords on Windows
This utility scans the passwords stored by popular Windows applications (Microsoft Outlook, Internet Explorer, Mozilla Firefox, and more...) and displays security information about all these passwords. The security information of every stored password includes the total number of characters, number of numeric characters, number of lowercase/uppercase characters, number of repeating characters, and password strength. You can use this tool to determine whether the passwords used by other users are secured enough, without watching the passwords themselves.
Start Using Password Security Scanner
Password Security Scanner doesn't require any installation process or additional dll files. In order to start using it, simply run the executable file - PasswordScan.exe
After you run PasswordScan.exe, Password Security Scanner scans the passwords stored on your system, and then displays the security information of all found passwords inside the main window.
You can also go to the 'Advanced Options' window (F9) and choose to displays only insecure passwords with low number of characters or with low password strength value.
Columns Description
- Item Name:The name of the item. For Web site passwords, the address of the Web site is displayed. For email passwords, the email address is displayed.
- Password Type:The type of the password: Web Browser, Messenger, Email, or Dialup/VPN.
- Application:The application that stores the specified password item: Microsoft Outlook, Firefox, Internet Explorer, and so on...
- User Name:The user name that is used with the specified password item.
- Password Length:The total number of characters in the password.
- Numeric:The total number of numeric characters (0 - 9) in the password.
- Lowercase:The total number of lowercase characters (a - z) in the password.
- Uppercase:The total number of uppercase characters (A - Z) in the password.
- Other Ascii:The total number of non-alphanumeric characters in the password.
- Non-English:The total number of non-English characters in the password.
- Repeating:The total number of repeating characters in the password. For example, if the password is abcdab, then the 'Repeating' value will be 2, because both a and b characters appears more than once.
- Password Strength:The strength of the password, calculated according to number of parameters, including the total number of characters, number of repeating characters, type of characters used in the passwords, and more...The numeric value displayed in this column represents the strength of the password, according to the following list:
- 1 - 7: Very Weak
- 8 - 14: Weak
- 15 - 25: Medium
- 26 - 45: Strong
- 46 and above: Very Strong
- Windows User:The Windows user that owns the password. For most passwords, this column will display the current logged-on user. However, for Dialup passwords of Windows, you might also see the passwords of other Windows users, and in those cases, this column will display the Windows users that created the dialup password.
↧
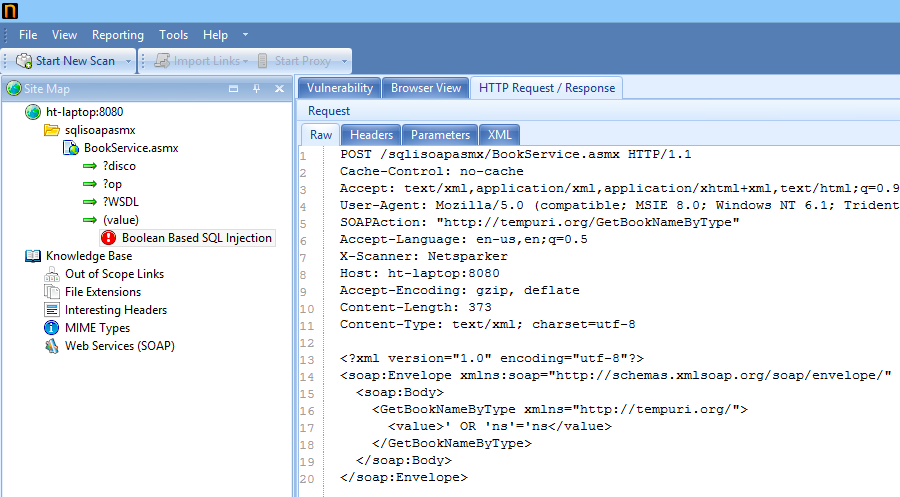
Netsparker v3.5 - Web Application Security Scanner
Netsparker Web Application Security Scanner can find and report web application vulnerabilities such as SQL Injection and Cross-site Scripting (XSS) and security issues on all web applications and websites regardless of the platform and the technology they are built on.
Netsparker is very easy to use and its unique detection and safe exploitation techniques allow it to be dead accurate in reporting hence it is the first and only False Positive Free web vulnerability scanner, therefore users can focus on remediating reported vulnerabilities and security issues without wasting time on learning how to use the web vulnerability scanner or verify its findings.
Changelog - 3.5.3
NEW FEATURES
* DOM based cross-site scripting vulnerability scanning* Chrome based web browser engine for DOM parsing
* URL rewrite rules configuration wizard (to scan parameters in URLs)
* "Ignore Vulnerability from Scan" option to exclude vulnerabilities from reports
NEW SECURITY TESTS
* Nginx web server Out-of-date version check* Perl possible source code disclosure
* Python possible source code disclosure
* Ruby possible source code disclosure
* Java possible source code disclosure
* Nginx Web Server identification
* Apache Web Server identification
* Java stack trace disclosure
IMPROVEMENTS
* Improved the correctness and coverage of Remote Code Execution via Local File Inclusion vulnerabilities* Improved cross-site scripting vulnerability confirmation patterns
* Added support for viewing JSON arrays in document roots in request/response viewers
* Added support for Microsoft Office ACCDB database file detection
* Improved DOM parser to exclude non-HTML files
* Improved PHP Source Code Disclosure vulnerability detection
* Improved Nginx Version Disclosure vulnerability template
* Improved IIS 8 Default Page detection
* Improved Email List knowledgebase report to include generic email addresses
* Improved Configure Form Authentication wizard by replacing embedded record browser with a Chrome based browser
* Improved the form authentication configuration wizard to handle cases where Basic/NTLM/Digest is used in conjunction with Form Authentication
* Added a cross-site scripting attack pattern which constructs a valid XHTML in order to trigger the XSS
* Added double encoded attack groups in order to reduce local file inclusion vulnerability confirmation requests
* Added status bar label which displays current VDB version and VDB version update notifications
* Added login activity indicator to Scan Summary Dashboard
* Added a new knowledgebase out-of-scope reason for links which exceed maximum depth
* Updated external references in cross-site scripting vulnerability templates
* Improved DOM parser by providing current cookies and referer to DOM/JavaScript context
* Added several new DOM events to simulate including keyboard events
* Improved the parsing of "Anti-CSRF token field names" setting by trimming each individual token name pattern
* Added support for simulating DOM events inside HTML frames/iframes
* Consolidated XSS exploitation function name (netsparker()) throughout all the areas reported
* Removed redundant semicolon followed by waitfor delay statements from time based SQLi attack patterns to bypass more blacklistings
* Changed default user-agent string to mimic a Chrome based browser
* Improved LFI extraction file list to extract files from target system according to detected OS
* Removed outdated PCI 1.2 classifications
FIXES
* Fixed indentation problem of bullets in knowledgebase reports* Fixed path disclosure reports in MooTools JavaScript file
* Fixed KeyNotFoundException occurs when a node from Sitemap tree is clicked
* Fixed NullReferenceException thrown from Boolean SQL Injection Engine
* Fixed an issue in WebDav Engine where an extra parameter is added when requesting with Options method
* Fixed a bug where LFI exploitation does not work for double encoded paths
* Fixed a bug in Export file dialog where .nss extension isn't appended if file name ends with a known file extension
* Fixed a bug in Configure Form Authentication wizard where the number of scripts loaded shows incorrectly
* Fixed a bug which occurs while retesting with CSRF engine
* Fixed a bug where retest does not work after loading a saved scan session
* Fixed a bug where Netsparker reports out of date PHP even though PHP is up to date
* Fixed a UI hang where Netsparker tries to display a binary response in Browser View tab
* Fixed an ArgumentNullException thrown when clicking Heartbleed vulnerability
* Fixed a bug where Netsparker makes requests to DTD URIs in XML documents
* Fixed a bug in Scan Policy settings dialog where list of user agents are duplicated
* Fixed a typo in ViewState MAC Not Enabled vulnerability template
* Fixed a bug in auto updater where the updater doesn't honour the AutoPilot and Silent command line switches
* Fixed XSS exploit generation code to handle cases where input name is "submit"
* Fixed a bug that prevents Netsparker.exe process from closing if you try to close Netsparker immediately after starting a new scan
* Fixed a UI hang happens when the highlighted text is huge in response source code
* Fixed issues with decoded HTML attribute values in text parser
* Fixed session cookie path issues according to how they are implemented in modern browsers
* Fixed scan stuck at re-crawling issue for imported scan sessions
* Fixed highlighting issues for possible XSS vulnerabilities
* Fixed a crash due to empty/missing URL value for form authentication macro requests
* Fixed a NullReferenceException in Open Redirect Engine which occurs if redirect response is missing Location header
* Fixed an error in authentication macro sequence player happens when the request URI is wrong or missing
↧
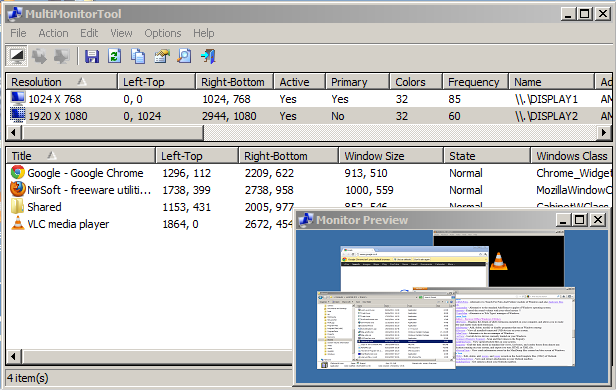
MultiMonitorTool v1.63 - Multiple Monitors on Windows
MultiMonitorTool is a small tool that allows you to do some actions related to working with multiple monitors. With MultiMonitorTool, you can disable/enable monitors, set the primary monitor, save and load the configuration of all monitors, and move windows from one monitor to another. You can do these actions from the user interface or from command-line, without displaying user interface. MultiMonitorTool also provides a preview window, which allows you to watch a preview of every monitor on your system.
Using MultiMonitorTool
MultiMonitorTool doesn't require any installation process or additional dll files. In order to start using it, simply run the executable file - MultiMonitorTool.exe
The main window of MultiMonitorTool contains 2 panes: The upper pane displays the list of all monitors detected on your system. When you select a monitor in the upper pane, the lower pane displays the details of all visible windows on the selected monitor.
You can select one or more monitors in the upper pane, and then use the following options: Disable Selected Monitors (Ctrl+F6), Enable Selected Monitors (Ctrl+F7), Disable/Enable Switch (Ctrl+F8), or Set As Primary Monitor (Ctrl+F9)
You can also select one or more Windows in the lower pane, and then use the 'Move Window To Next Monitor' and 'Move Window To Primary Monitor' options in order to easily move Windows from one monitor to the other.
Save/Load Monitors Configuration
MultiMonitorTool allows you to save the current configuration of all monitors on your system, including the screen resolution, colors depth, and monitor position of every monitor, by using the 'Save Monitors Configuration' option (Ctrl+Shift+S).You can restore back the saved monitors configuration by using the 'Load Monitors Configuration' option (Ctrl+Shift+L).
You can also save/load the monitors configuration from command-line, by using the /SaveConfig and /LoadConfig command-line options.
Preview Window
The preview window shows you a preview of the monitor you select in the upper pane. It might be useful if non-primary monitors are turned off and you want to view the windows displayed in the other monitors. In order to enable/disable the monitor preview window, simply press F2. You can also resize the preview window to any size you like.
Command-Line Options
You can use the following command-line options to change the monitor configuration or to move windows automatically without displaying any user interface.The <Monitor> parameter in all command-line options may contain the following values:
- Primary - Specifies that you want to do the action on the primary monitor.
- Monitor Name, as it appears in the 'Name' column, for example: \\.\DISPLAY1 , \\.\DISPLAY2, \\.\DISPLAY3
- Monitor Number - The number that appears in the monitor name. (1 for \\.\DISPLAY1, 2 for \\.\DISPLAY2, and so on...)
| /disable <Monitors> | Disables the specified monitors. You can specify a single monitor or multiple monitors. Examples: MultiMonitorTool.exe /disable 1 MultiMonitorTool.exe /disable \\.\DISPLAY3 MultiMonitorTool.exe /disable 1 2 3 |
| /enable <Monitors> | Enables the specified monitors. Examples: MultiMonitorTool.exe /enable 3 MultiMonitorTool.exe /enable \\.\DISPLAY1 MultiMonitorTool.exe /enable 3 2 |
| /switch <Monitors> | Switches the specified monitors between enabled and disabled state. Examples: MultiMonitorTool.exe /switch 3 MultiMonitorTool.exe /switch \\.\DISPLAY1 MultiMonitorTool.exe /switch \\.\DISPLAY2 \\.\DISPLAY3 |
| /setmax <Monitors> | Set the maximum resolution on the specified monitors. Examples: MultiMonitorTool.exe /setmax 3 MultiMonitorTool.exe /setmax \\.\DISPLAY2 \\.\DISPLAY3 |
| /SetOrientation <Monitor> <Orientation [0, 90, 180, 270] > | Set the orientation of the specified monitor. Examples: MultiMonitorTool.exe /SetOrientation 2 270 MultiMonitorTool.exe /SetOrientation \\.\DISPLAY2 180 \\.\DISPLAY3 90 MultiMonitorTool.exe /SetOrientation 1 0 2 0 |
| /SetPrimary <Monitor> | Set the primary monitor. Examples: MultiMonitorTool.exe /SetPrimary 2 MultiMonitorTool.exe /SetPrimary \\.\DISPLAY2 |
| /SetNextPrimary | Set the next available monitor as the primary monitor. For example, if you have a system with 3 monitors and the first monitor is the primary, running this command will set the second monitor as the primary. running this command again will set the third monitor as the primary. And... running this command again will set (again) the first monitor as the primary. |
| /PreviewOnly <Monitor> {x} {y} {width} {height} | Allows you to run MultiMonitorTool in monitor preview only mode. In this mode, only the monitor preview window is displayed. You must specify the monitor name to display in the preview window. Optionally, you can also specify the position and size to set the preview window. Examples: MultiMonitorTool.exe /PreviewOnly \\.\DISPLAY2 MultiMonitorTool.exe /PreviewOnly \\.\DISPLAY1 10 10 300 200 |
| /SaveConfig <Filename> | Saves the current configuration of all your monitors into the specified filename, including the screen resolution, colors depth, and monitor position. You can load the saved configuration back into the system by using the /LoadConfig command-line option. Example: MultiMonitorTool.exe /SaveConfig "c:\temp\monitors1.cfg" |
| /LoadConfig <Filename> | Loads the monitors configuration that you previouly saved with /SaveConfig Example: MultiMonitorTool.exe /LoadConfig "c:\temp\monitors1.cfg" |
/MoveWindow <To Monitor> Process <Process Name> /MoveWindow <To Monitor> Title <Title Text> /MoveWindow <To Monitor> Class <Window Class> /MoveWindow <To Monitor> All <From Monitor> | This command-line allows you to move windows from one monitor to the other, according to the specified conditions. You can also use this command-line option with /WindowLeft, /WindowTop, /WindowWidth, and /WindowHeight, in order to set the width/size of the moved window. (See examples below) Here's some example:
|
| /MonitorPreviewWindow <0 | 1> | Specifies whether to display the monitor preview window. 0 = No, 1 = Yes. |
| /PreviewMode <1 | 2> | Specifies the preview mode. 1 = Fast and Low Quality, 2 = Slow and High Quality. |
| /DrawCursorPreview <0 | 1> | Specifies whether to draw the cursor inside the preview window. 0 = No, 1 = Yes. |
| /HideInactiveMonitors <0 | 1> | Specifies whether to hide inactive monitors. 0 = No, 1 = Yes. |
| /TrayIcon <0 | 1> | Specifies whether to put an icon on the system tray. 0 = No, 1 = Yes. |
| /StartAsHidden <0 | 1> | Specifies whether to start the main window as hidden. 0 = No, 1 = Yes. Ths command-line option works only when TrayIcon option is turned on. |
| /AutoRefresh <0 | 1> | Specifies whether to automatically refresh the monitors/windows information. 0 = No, 1 = Yes. |
| /stext <Filename> | Save the monitors list into a regular text file. |
| /stab <Filename> | Save the monitors list into a tab-delimited text file. |
| /scomma <Filename> | Save the monitors list into a comma-delimited text file (csv). |
| /stabular <Filename> | Save the monitors list into a tabular text file. |
| /shtml <Filename> | Save the monitors list into HTML file (Horizontal). |
| /sverhtml <Filename> | Save the monitors list into HTML file (Vertical). |
| /sxml <Filename> | Save the monitors list to XML file. |
↧
PacketFence v4.3.0 - Free and Open Source network access control (NAC) solution
PacketFence is a fully supported, trusted, Free and Open Source network access control (NAC) solution. Boasting an impressive feature set including a captive-portal for registration and remediation, centralized wired and wireless management, powerful BYOD management options, 802.1X support, layer-2 isolation of problematic devices; PacketFence can be used to effectively secure networks small to very large heterogeneous networks.
Here are the changes in 4.3.0:
New Features
- Added MAC authentication support for Edge-corE 4510
- Added support for Ruckus External Captive Portal
- Support for Huawei S2700, S3700, S5700, S6700, S7700, S9700 switches
- Added support for LinkedIn and Windows Live as authentication sources
- Support for 802.1X on Juniper EX2200 and EX4200 switches
- Added support for the Netgear M series switches
- Added support to define SNAT interface to use for passthrough
- Added Nessus scan policy based on a DHCP fingerprint
- Added support to unregister a node if the username is locked or deleted in Active Directory
- Fortinet FortiGate and PaloAlto firewalls integration
- New configuration parameters in switches.conf to use mapping by VLAN and/or mapping by role
Enhancements
- When validating an email confirmation code, use the same portal profile initially used by to register the device
- Removed old iptables code (ipset is now always used for inline enforcement)
- MariaDB support
- Updated WebAPI method
- Use Webservices parameters from PacketFence configuration
- Use WebAPI notify from pfdhcplistener (faster)
- Improved Apache SSL configuration forbids SSLv2 use and prioritzes better ciphers
- Removed CGI-based captive portal files
- For device registration use the source used to authenticate for calculating the role and unregdate (bugid:1805)
- For device registration, we set the "NOTES" field of the node with the selected type of device (if defined)
- On status page check the portal associated to the user and authenticate on the sources included in the portal profile
- Merge pf::email_activation and pf::sms_activation to pf::activation
- Removed unused table switchlocation
- Deauthentication and firewall enforcement can now be done throught the web API
- Added support to configure high-availability from within the configurator/webadmin
- Changed the way we’re handling DNS blackholing when unregistered in inline enforcement mode (using DNAT rather than REDIRECT)
- Now handling rogue DHCP servers based both on the server IP and server MAC address
Bug Fixes
- Fixed pfdetectd not starting because of stale pid file
- Fixed SQL join with iplog in advanced search of nodes
- Fixed unreg date calculation in Catalyst captive portal
- Fixed allowed_device_types array in device registration page (bugid:1809)
- Fixed VLAN format to comply with RFC 2868
- Fixed possible double submission of the form on the billing page
- Fixed db upgrade script to avoid duplicate changes to locationlog table
See the ChangeLog file for the complete list of changes.
See the UPGRADE file for notes about upgrading.
↧
↧
FolderTimeUpdate - Tool that scans all files and folders and updates the Modified Time of every folder according the latest modified time
FolderTimeUpdate is a simple tool for Windows that scans all files and folders under the base folder you choose, and updates the 'Modified Time' of every folder according the latest modified time of the files stored in it.
This tool might be useful if, for example, you backup a cluster of folders and then restore them into another disk, but the backup program doesn't restore the original modified time of the folders.
Start Using FolderTimeUpdate
FolderTimeUpdate doesn't require any installation process or additional dll files. In order to start using it, simply run the executable file - FolderTimeUpdate.exe
After running FolderTimeUpdate, you can choose the desired base folder and the other options and then click the 'Start' button to start updating the modified time of all folders.
If you're not totally sure that the 'Modified Time' change is right for you, you can choose the 'Simulation Mode' option. When 'Simulation Mode' is on, FolderTimeUpdate will only display the changes of the modified time that will be made for all folders, but without actually applying these changes.
↧
NoVirusThanks File Governor - Unlock locked files and folders
NoVirusThanks File Governor is an advanced program which allows for files and folders within the system to be unlocked so that normal file I/O operations can be completed when normally they would not be able to be due to operating system restrictions for files currently in use. Once a file or folder is unlocked you will be able to force-close the file’s handle, rename, delete, etc.
I am sure that at least one time, you have run into a situation where you wanted to delete a file, but Windows wouldn’t allow you to do it because the file was already in use by another program or because the access to the file you wanted to delete was denied for some reasons. In this case you should know these messages:
- The source or destination file may be in use
- Cannot delete file: Access is denied
- The file is in use by another program or user
- There has been a sharing violation
- Make sure the disk is not full or write-protected
You can use NoVirusThanks File Governor to safely close all the opened handles of a file or to safely close all the opened files inside a folder so that you will be able to delete the files and the folder without problems. This tool is useful also to unlock files locked by malware or unload malicious DLL files.
Key features and characteristics
- Unblock files and folders locked by other applications
- Terminate processes that lock a file or folder
- Scan files and folders for locked objects
- Close opened handles and unload loaded DLL modules
- Unload DLL modules loaded in running processes
- Unlock all locked objects with a single mouse click
- Scan files and folders through the Windows explorer context menu
- Safely delete a locked file on the next reboot
- A valid and powerful alternative to the popular Unlocker
- Run it from the USB flash drive with the portable version
- The application can be translated into multiple languages
- Supports all Microsoft Windows operating systems
- Very lightweight in the memory and CPU usage
↧
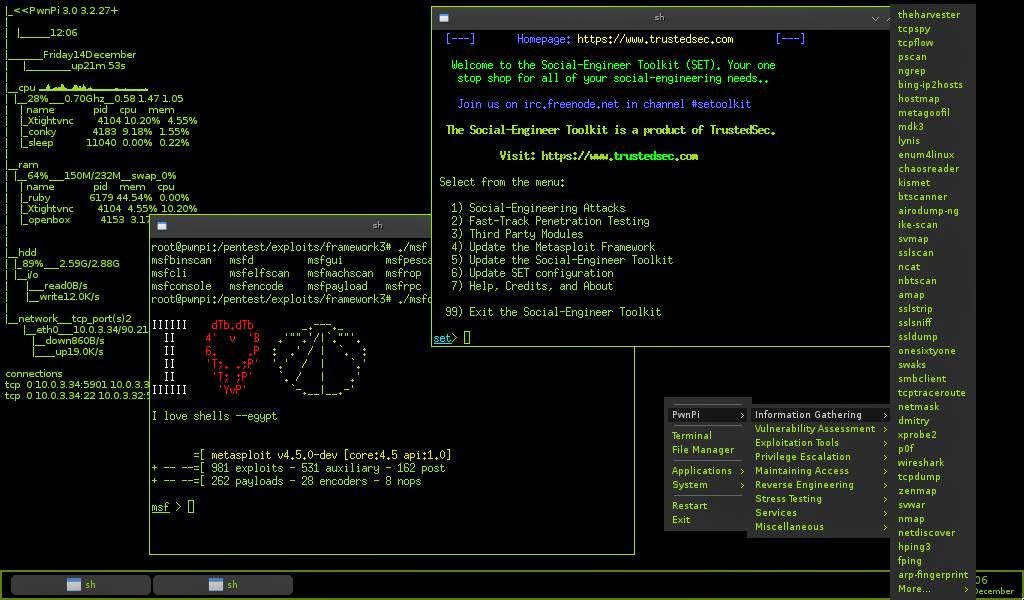
PwnPi - A Pen Test Drop Box distro for the Raspberry Pi
PwnPi is a Linux-based penetration testing dropbox distribution for the Raspberry Pi. It currently has 200+ network security tools pre-installed to aid the penetration tester. It is built a stripped down version of the Debian Wheezy image from the Raspberry Pi foundation's website and uses Openbox as the window manager. PwnPi can be easily setup to send reverse connections from inside a target network by editing a simple configuration file.
Tools:
6tunnel - TCP proxy for non-IPv6 applications
aircrack-ng - WEP/WPA cracking program
amap - a powerful application mapper
arp-scan - arp scanning and fingerprinting tool
bfbtester - Brute Force Binary Tester
bing-ip2hosts - Enumerate hostnames for an IP using bing
bsqlbf - Blind SQL injection brute forcer tool
btscanner - ncurses-based scanner for Bluetooth devices
chaosreader - trace network sessions and export it to html format
chkrootkit - rootkit detector
cryptcat - A lightweight version netcat extended with twofish encryption
darkstat - network traffic analyzer
dhcpdump - Parse DHCP packets from tcpdump
dissy - graphical frontend for objdump
dmitry - Deepmagic Information Gathering Tool
dns2tcp - TCP over DNS tunnel client and server
dnswalk - Checks dns zone information using nameserver lookups
dsniff - Various tools to sniff network traffic for cleartext insecurities
enum4linux - a tool for enumerating information from Windows and Samba systems
etherape - graphical network monitor
exploit-db - Exploit Database
fcrackzip - password cracker for zip archives
fimap - local and remote file inclusion tool
flasm - assembler and disassembler for Flash (SWF) bytecode
foremost - forensic program to recover lost files
fping - sends ICMP ECHO_REQUEST packets to network hosts
ftp-proxy - application level proxy for the FTP protocol
galleta - An Internet Explorer cookie forensic analysis tool
ghettotooth - a simple but effective blue driving tool
hostmap - hostnames and virtual hosts discovery tool
hping3 - Active Network Smashing Tool
httptunnel - Tunnels a data stream in HTTP requests
httrack - Copy websites to your computer (Offline browser)
hydra - Very fast network logon cracker
ike-scan - discover and fingerprint IKE hosts (IPsec VPN Servers)
inguma - Open source penetration testing toolkit
iodine - tool for tunneling IPv4 data through a DNS server
ipcalc - parameter calculator for IPv4 addresses
isr-evilgrade - take advantage of poor upgrade implementations by injecting fake updates
ipgrab - tcpdump-like utility that prints detailed header information
john - active password cracking tool
kismet - Wireless 802.11b monitoring tool
knocker - Simple and easy to use TCP security port scanner
lcrack - A generic password cracker
lynis - security auditing tool for Unix based systems
macchanger - utility for manipulating the MAC address of network interfaces
mboxgrep - Grep through mailboxes
mdk3 - bruteforce SSID's, bruteforce MAC filters, SSID beacon flood
medusa - fast, parallel, modular, login brute-forcer for network services
metagoofil - an information gathering tool designed for extracting metadata
metasploit - security project which provides information about security vulnerabilities
mysqloit - SQL Injection takeover tool focused on LAMP
mz - versatile packet creation and network traffic generation tool
nbtscan - A program for scanning networks for NetBIOS name information
netcat-traditional - TCP/IP swiss army knife
netdiscover - active/passive network address scanner using arp requests
netrw - netcat like tool with nice features to transport files over network
netsed - network packet-altering stream editor
netwag - graphical frontend for netwox
netwox - networking utilities
nikto - web server security scanner
nmapsi4 - graphical interface to nmap, the network scanner
nmap - The Network Mapper
nstreams - network streams - a tcpdump output analyzer
obexftp - file transfer utility for devices that use the OBEX protocol
onesixtyone - fast and simple SNMP scanner
openvas-client - Remote network security auditor, the client
openvas-server - remote network security auditor - server
ophcrack-cli - Microsoft Windows password cracker using rainbow tables (cmdline)
ophcrack - Microsoft Windows password cracker using rainbow tables (gui)
otp - Generator for One Time Pads or Passwords
p0f - Passive OS fingerprinting tool
packeth - Ethernet packet generator
packit - Network Injection and Capture
pbnj - a suite of tools to monitor changes on a network
pentbox - Suite that packs security and stability testing oriented tools
pdfcrack - PDF files password cracker
pnscan - Multi threaded port scanner
proxychains - proxy chains - redirect connections through proxy servers
pscan - Format string security checker for C files
ptunnel - Tunnel TCP connections over ICMP packets
ratproxy - passive web application security assessment tool
reaver - brute force attack tool against Wifi Protected Setup PIN number
s.e.t - social engineering toolkit
scrub - writes patterns on magnetic media to thwart data recovery
secure-delete - tools to wipe files, free disk space, swap and memory
sendemail - lightweight, command line SMTP email client
siege - HTTP regression testing and benchmarking utility
sipcrack - SIP login dumper/cracker
sipvicious - suite is a set of tools that can be used to audit SIP based VoIP systems
skipfish - fully automated, active web application security reconnaissance tool
socat - multipurpose relay for bidirectional data transfer
splint - tool for statically checking C programs for bugs
sqlbrute - a tool for brute forcing data out of databases using blind SQL injection
sqlmap - tool that automates the process of detecting and exploiting SQL injection flaws
sqlninja - SQL Server injection and takeover tool
ssldump - An SSLv3/TLS network protocol analyzer
sslscan - Fast SSL scanner
sslsniff - SSL/TLS man-in-the-middle attack tool
sslstrip - SSL/TLS man-in-the-middle attack tool
stunnel4 - Universal SSL tunnel for network daemons
swaks - SMTP command-line test tool
tcpdump - command-line network traffic analyzer
tcpflow - TCP flow recorder
tcpick - TCP stream sniffer and connection tracker
tcpreplay - Tool to replay saved tcpdump files at arbitrary speeds
tcpslice - extract pieces of and/or glue together tcpdump files
tcpspy - Incoming and Outgoing TCP/IP connections logger
tcptrace - Tool for analyzing tcpdump output
tcpxtract - extracts files from network traffic based on file signatures
theHarvester - gather emails, subdomains, hosts, employee names, open ports and banners
tinyproxy - A lightweight, non-caching, optionally anonymizing HTTP proxy
tor - anonymizing overlay network for TCP
u3-tool - tool for controlling the special features of a U3 USB flash disk
udptunnel - tunnel UDP packets over a TCP connection
ussp-push - Client for OBEX PUSH
vidalia - controller GUI for Tor
vinetto - A forensics tool to examine Thumbs.db files
voiphopper - VoIP infrastructure security testing tool
voipong - VoIP sniffer and call detector
w3af-console - framework to find and exploit web application vulnerabilities (CLI only)
w3af - framework to find and exploit web application vulnerabilities
wapiti - Web application vulnerability scanner
wash - scan for vunerable WPS access points
wavemon - Wireless Device Monitoring Application
wbox - HTTP testing tool and configuration-less HTTP server
webhttrack - Copy websites to your computer, httrack with a Web interface
weplab - tool designed to break WEP keys
wfuzz - a tool designed for bruteforcing Web Applications
wipe - Secure file deletion
wireshark - network traffic analyzer - GTK+ version
xprobe - Remote OS identification
yersinia - Network vulnerabilities check software
zenmap - The Network Mapper Front End
zzuf - transparent application fuzzer
↧
Inxi - A newer, better system information script for irc, administration, and system troubleshooters
A newer, better system information script for irc, administration, and system troubleshooters.
Inxi Options
Inxi has a wide range of options and custom triggers, along with useful defaults like -b or -F. Plain inxi, no options, prints a single line of basic system information.
Here is a screenshot of typical output for inxi -Fz (-z filters certain output like IP numbers and Mac address of network card, things that don't need to be publically displayed for security reasons). The display output has changed slightly as of 1.7.x:
Full List of Inxi Options
- inxi supports the following options. These options are included as of inxi 2.2.20. Earlier versions may not have every option. You can combine these options, or list them one by one: Examples: inxi -v4 -c6 OR inxi -bDc 6
- If you start inxi with no arguments, it will show the short form. The following options if used without -b, -F or -v + number will show just that complete line:
- A, C, D, G, I, M, N, P, R, S, f, i, n, o, p, l, u, r, s, t, w, W - you can use these together or alone to show just the line(s) you want to see.
- If you use them with either a -v + level, a -b, or with -F, it will show the full output for that line along with the output for the chosen verbosity level.
- NOTE: as of version 1.6.5, the old basic output option -d was changed to -b, for basic. -d is now used for the extended disk option, showing cdrom/dvd information as well.
- Output Control Options:
- -A Show Audio/sound card information.
- -b Shows basic (b for basic - version 1.7.5 or later. Earlier versions used: -d) output, short form. Similar to inxi -v 2. Shows -S -M -C -G -N -D and -R (short forms), and -I. -R does not show if no raid devices found.
- -c Available color schemes. Scheme number is required. Color selectors run a color selector option prior to inxi starting which lets you set the config file value for the selection.
- Supported color schemes: 0-32 Example: inxi -c 11
- Note: if you want to turn off all script colors, use -c 0 This is useful if you are for example piping output and don't want the color code characters.
- Supported color selectors. NOTE: irc and global only show safe color set. (version 1.5.x or later only)
- 94 - Console, out of X
- 95 - Terminal, running in X - like xTerm
- 96 - Gui IRC, running in X - like Xchat, Quassel, Konversation etc.
- 97 - Console IRC running in X - like irssi in xTerm
- 98 - Console IRC not in X
- 99 - Global - Overrides/removes all settings. Setting specific removes global.
- -C Show full CPU output, including per CPU clockspeed.
- -D Show full hard Disk info, not only model, ie: /dev/sda ST380817AS 80.0GB.
- -f Show all cpu flags used, not just the short list. Not shown with -F to avoid spamming.
- -F Show Fuller output for inxi, includes all upper case line arguments, plus -n and -s. Does not show extra verbose options like -d -f -u -l -p -t or -o unless you add them explicitly, for example: -Fplo
- -G Show Graphic card information (card, x type, resolution, version). Also shows glx renderer, card pci busID with -x. Shows active/unloaded/failed driver versions (1.5.x or later)
- -i Show Wan IP address, and shows local interfaces (requires ifconfig network tool). Same as -Nni
- If you are going to use this for public posting of your data, consider running it with the -z option for filtering. IRC filters by default.
- -I (upper case i) Show Information: processes, uptime, memory, irc client, inxi version.
- -l (lower case l, el) Show partition labels. Default: short partition -P. For full -p output, use: -pl (or -plu).
- -M Show machine data. Motherboard, Bios, and if present, System Builder (Like Lenovo) (version 1.6.x and later). Older systems/kernels without the required /sys data can use dmidecode instead, run as root. -! 33 forces use of dmidecode, which might be of some utility in certain fringe cases where dmidecode has more data than /sys.
- -n Show Advanced Network card information. Same as -Nn. Shows interface, speed, mac id, state (version 1.5.x and later).
- -N Show Network card information. Shows card and driver. Includes support for USB networking devices. Also shows busID/USB-ID, ports, driver version with -x
- -o Show unmounted partition information (includes UUID and LABEL if available).
- Shows file system type if you have file installed, if you are root OR if you have added to /etc/sudoers (sudo v. 1.7 or newer):
- < username > ALL = NOPASSWD: /usr/bin/file (sample)
- -p Show full partition information (-P plus all other detected partitions).
- -P Show Partition information (shows what -v 4 would show, but without extra data).
- Shows, if detected: / /boot /home /tmp /usr /var. Use -p to see all mounted partitions.
- -r Show distro repository data. Currently supported repo types:
- APT (Debian, Ubuntu + derived versions)
- PACMAN (Arch Linux + derived versions)
- PISI (Pardus + derived versions)
- URPMQ (Mandriva, Mageia + derived versions)
- YUM. (Fedora, Redhat, maybe Suse + derived versions)
- (as distro data is collected more will be added. If your's is missing please show us how to get this information and we'll try to add it.)
- -R Show RAID data. Shows RAID devices, states, levels, and components, and extra data with -x/-xx. If device is resyncing, shows resync progress line as well.
- -s Show sensors output (if sensors installed/configured): mobo/cpu/gpu temp; detected fan speeds.
- Gpu temp only for Fglrx/Nvidia drivers. Nvidia shows screen number for > 1 screens
- -S Show System information: host name, kernel, desktop, desktop version (plus toolkit if -x used), distro (desktop features, version 1.5.x or later)
- -t Show processes. Requires extra options: c (cpu) m (memory) cm (cpu+memory).
- If followed by numbers 1-20, shows that number of top process for each selection (default: 5):
- Examples:
- -t cm10 (shows top 10 cpu and memory processes, 20 in all)
- -t c (shows top 5 cpu processes)
- -t m20 (shows top 20 memory processes)
- -t cm (shows top 5 cpu and memory processes, 10 in all)
- Make sure to have no space between letters and numbers (cm10 -right, cm 10 - wrong).
- -u Show partition UUIDs. Default: short partition -P. For full -p output, use: -pu (or -plu).
- -v Script verbosity levels. Verbosity level number is required. Note: do not mix -v options with -b or -F, use one or the other.
- Supported levels: 0-7 Example: inxi -v 4
- 0 - short output, same as: inxi
- 1 - Basic verbose. Roughly the same as the old -d,
- 2 - Adds networking card (-N), Machine (-M) data, and shows basic hard disk data (names only), and basic raid (devices only, and if inactive, notes that). Similar to inxi -b
- 3 - Adds advanced CPU (-C), network (-n) data, and switches on -x advanced data option.
- 4 - Adds partition size/filled data (-P) for (if present):/, /home, /var/, /boot. Shows full disk data (-D)
- 5 - Adds audio card (-A); sensors (-s), partition label (-l) and UUID (-u), short form of optical drives, and standard raid data (-R).
- 6 - Adds full partition data (-p), unmounted partition data (-o), -d full disk data, including CD/DVD information.
- 7 - Adds network IP data (-i); triggers -xx.
- -w Local weather data/time. To check an alternate location, see: -W location. For extra weather data options see -x, -xx, and -xxx.
- -W location - location supported options: postal code; city,[state/country]; latitude,longitude. Only use if you want the weather somewhere other than the machine running inxi. Use only ascii characters, replace spaces in city/state/country names with +: new+york,ny
- -x Show extra data:
- -C - Bogomips on Cpu; CPU flags short list
- -d - Shows more information if present on cd/dvd devices.
- -D - Shows hdd temp with disk data if you have hddtemp installed, if you are root OR if you have added to /etc/sudoers (sudo v. 1.7 or newer):
- < username > ALL = NOPASSWD: /usr/sbin/hddtemp (sample)
- -G - Direct rendering status for Graphics (in X). Only works with verbose or line output;
- -G - Shows (for single gpu, nvidia driver) screen number gpu is running on.
- -i - Show IPv6 as well for LAN interface (IF) devices.
- -I - Show system GCC, default. With -xx, also show other installed GCC versions. Show Init type, if detected, like systemd, Upstart, SysVinit, init (bsd), Epoch, runit. Show runlevel/target if present.
- -N, -A - driver version (if available) for Network/Audio;
- -N, -A - Shows port for card/device, if available.
- -N -A -G - Shows pci Bus ID / Usb ID for Audio, Network, Graphics
- -R - Shows component raid id. Adds second RAID Info line: raid level; report on drives (like 5/5); blocks; chunk size; bitmap (if present). Resync line, shows blocks synced/total blocks.
- -S - Shows toolkit (QT or GTK) if GNOME, KDE, or XFCE. Shows kernel gcc version.
- -t - Adds memory use output to cpu (-xt c, and cpu use to memory (-xt m).
- -w/-W - Wind speed and time zone (time zone, -w only).
- -xx Show extra, extra data (only works with verbose or line output, not short form). You can also trigger it with -Fx (but not -xF) (Version 1.6.x and later)
- -D - Adds disk serial number.
- -I - Adds other detected installed gcc versions to primary gcc output (if present). Shows init type version if found, and default runlevel/target if found.
- -M - Adds chassis information, if any data for that is available.
- -N -A -G - Shows vendor:product ID for Audio, Network, Graphics
- -R - Adds superblock (if present); algorythm, U data. Adds system info line (kernel support, read ahead, raid events). Adds if present, unused device line. Resync line, shows progress bar.
- -w/-W - Humidity, barometric pressure.
- -xx -@ [11-14] - Automatically uploads debugger data tar.gz file to ftp.techpatterns.com.
- -xxx Show extra, extra, extra data (only works with verbose or line output, not short form):
- -S - Panel/shell information in desktop output, if in X (like gnome-shell, cinnamon, mate-panel).
- -w/-W - Location (uses -z/irc filter), weather observation time, wind chill, heat index, dew point (shows extra lines for data where relevant).
- -y (plus integer >= 80) This is an absolute width override which sets the output line width max. Overrides COLS_MAX_IRC / COLS_MAX_CONSOLE globals, or the actual widths of the terminal. If used with -h or -c 94-99, put -y option first or the override will be ignored. Cannot be used with --help / --version / --recommends type long options. Example: inxi -y 130 -Fxx
- -z Adds security filters for IP addresses, Mac, and user home directory name. Default on for irc clients.
- -Z Absolute override for output filters. Useful for debugging networking issues in irc for example.
- Additional Options:
- -h, --help This help menu.
- -H - This help menu, plus developer options. Do not use dev options in normal operation!
- --recommends Checks inxi application dependencies + recommends, and directories, then shows what package(s) you need to install to add support for that feature (version 1.6.6 and later).
- -U Auto-update script. Note: if you installed as root, you must be root to update, otherwise user is fine.
- -V, --version inxi version information. Prints information then exits.
- -% Overrides defective or corrupted data.
- -@ Triggers debugger output. Requires debugging level 1-13 (8-10 - logging). Less than 8 just triggers inxi debugger output on screen.
- 1-7 - On screen debugger output
- 8 - Basic logging
- 9 - Full file/sys info logging
- 10 - Color logging.
- The following create a tar.gz file of system data, plus collecting the inxi output to file. To automatically upload debugger data tar.gz file to ftp.techpatterns.com: inxi -xx@ [11-14] For alternate ftp upload locations: Example: inxi -! ftp.yourserver.com/incoming -xx@ 14
- 11 - With data file of xiin read of /sys.
- 12 - With xorg conf and log data, xrandr, xprop, xdpyinfo, glxinfo etc.
- 13 - With data from dev, disks, partitions etc.
- 14 - Everything, all the data available.
- -! 31 - Turns off hostname in output. Useful if showing output from servers etc.
- -! 32 - Turns on hostname in output. Overrides global B_SHOW_HOST='false'
- -! 33 - Force use of dmidecode. This will override /sys data in some lines, like -M.
↧
↧
aNmap - Android Network Mapper (Nmap for Android)
Nmap is one of the most improtant tools for every cracker (white, grey black hat "hacker"). Nmap is a legendary hack tool and probably the prevelent networt security port scanner tool over the last 10 years on all major Operating Systems. So far it was available in windows, linux and Mac OS X. But now its available at android platform too. It is compiled from real Nmap source code by some developers to provide the support for android devices.
↧
Kautilya 0.5.0 - Passwords in Plain, Exfiltrate SAM, Code Exec and more
Kautilya is a toolkit which provides various payloads for a Human Interface Device which may help in breaking in a computer during penetration tests.
List of Payloads
Windows
Gather
- Gather Information
- Hashdump and Exfiltrate
- Keylog and Exfiltrate
- Sniffer
- WLAN keys dump
- Get Target Credentials
- Dump LSA Secrets
- Dump passwords in plain
- Copy SAM (VSS)
- Dump Process Memory
- Dump Windows Vault Credentials
Execute
- Download and Execute
- Connect to Hotspot and Execute code
- Code Execution using Powershell
- Code Execution using DNS TXT queries
- Download and Execute PowerShell Script
- Execute ShellCode
Backdoor
- Sethc and Utilman backdoor
- Time based payload execution
- HTTP backdoor
- DNS TXT Backdoor
- Wireless Rogue AP
- Tracking Target Connectivity
Escalate
- Remove Update
- Forceful Browsing
Manage
- Add an admin user
- Change the default DNS server
- Edit the hosts file
- Add a user and Enable RDP
- Add a user and Enable Telnet
- Add a user and Enable Powershell Remoting
Misc
- Browse and Accept Java Signed Applet
- Speak on Target
Linux
- Download and Execute
- Reverse Shells using built in tools
- Code Execution
- DNS TXT Code Execution
- Perl reverse shell (MSF)
OSX
- Download and Execute
- DNS TXT Code Execution
- Perl Reverse Shell (MSF)
- Ruby Reverse Shell (MSF)
Payloads Compatibility
- The Windows payloads and modules are written mostly in powershell (in combination with native commands) and are tested on Windows 7 and Windows 8.
- The Linux payloads are mostly shell scripts (those installed by default) in combination with commands. These are tested on Ubuntu 11.
- The OS X payloads are shell scripts (those installed by default) with usage of native commands. Tested on OS X Lion running on a VMWare
0.5.0
- Added Execute Shellcode for Windows (under Execution menu).
- Added "Dump passwords in plain" for Windows (under Gather menu).
- Added "Copy SAM (VSS)" for Windows (under Gather menu).
- Added "Dump Process Memory" for Windows (under Gather menu).
- Added "Dump Windows Vault Credentials" for Windows (under Gather menu).
- Added "Add a user and Enable Powershell Remoting" for Windows (under Manage menu).
- Added support for Gems bundler.
- Added more banners of Kautilya.
↧
Tor Browser 3.6.3 - Use Tor on Windows, Mac OS X, or Linux without needing to install any software
The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access sites which are blocked.
The Tor Browser lets you use Tor on Windows, Mac OS X, or Linux without needing to install any software. It can run off a USB flash drive, comes with a pre-configured web browser to protect your anonymity, and is self-contained.
Here is the complete changelog:
- All Platforms
- Update Firefox to 24.7.0esr
- Update obfsproxy to 0.2.12
- Update FTE to 0.2.17
- Update NoScript to 2.6.8.33
- Update HTTPS Everywhere to 3.5.3
- Bug 12673: Update FTE bridges
- Update Torbutton to 1.6.11.0
- Bug 12221: Remove obsolete Javascript components from the toggle era
- Bug 10819: Bind new third party isolation pref to Torbutton security UI
- Bug 9268: Fix some window resizing corner cases with DPI and taskbar size.
- Linux:
- Bug 11102: Set Window Class to "Tor Browser" to aid in Desktop navigation
- Bug 12249: Don't create PT debug files anymore
↧