![]()
Backdoors win32 PE files, to continue normal file execution (if the shellcode supports it), by patching the exe/dll directly.
Some executables have built in protections, as such this will not
work on all PE files. It is advisable that you test target PE files
before deploying them to clients or using them in exercises.
Win32 binaries now run on x64 working with ASLR for proper continued execution after shellcode has run.
Recently tested on all 32bit Sysinternal tools
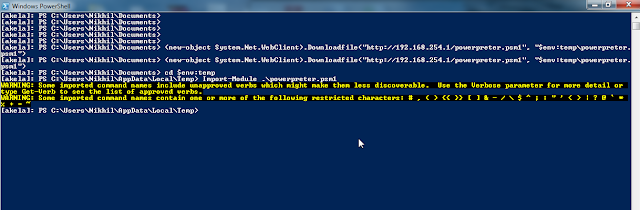
Usage: ./backdoor.py -h
Usage: backdoor.py [options]
Options:
-h, --help show this help message and exit
-f FILE, --file=FILE File to backdoor
-i HOST, --hostip=HOST
IP of the C2 for reverse connections
-p PORT, --port=PORT The port to either connect back to for reverse shells
or to listen on for bind shells
-o OUTPUT, --output-file=OUTPUT
The backdoor output file
-s SHELL, --shell=SHELL
Payloads that are available for use.
-n NSECTION, --section=NSECTION
New section name must be less than seven characters
-c, --cave The cave flag will find code caves that can be used
for stashing shellcode. This will print to all
the code caves of a specific size. The -l flag can be
use with this setting.
-d DIR, --directory=DIR
This is the location of the files that you want to
backdoor. You can make a directory of file backdooring
faster by forcing the attaching of a codecave to the
exe by using the -a setting.
-v, --verbose For debug information output.
-e ENCODER, --encoder=ENCODER
Encoders that can help with AV evasion.
-l SHELL_LEN, --shell_length=SHELL_LEN
For use with -c to help find code caves of different
sizes
-a, --add_new_section
Mandating that a new section be added to the exe
(better success) but less av avoidance
-w, --change_access This flag changes the section that houses the codecave
to RWE. Sometimes this is necessary. Enabled by
default. If disabled, the backdoor may fail.
-j, --injector This command turns the backdoor factory in a hunt and
shellcode inject type of mechinism. Edit the target
settings in the injector module.
-u SUFFIX, --suffix=SUFFIX
For use with injector, places a suffix on the original
file for easy recovery
-D, --delete_original
For use with injector module. This command deletes
the original file. Not for use in production systems.
Author not responsible for stupid uses.
Features:
-After making a copy of the target file, the file copy will be patched directly.
-Finding all codecaves in an EXE/DLL.
-Injecting modified reverse/bind shells that allow continued execution after connection to the attacker.
-Modifying the PE/COFF header to add an additional section for all win32 executables/dlls, including those with an import table.
-Using the existing shellcode options, the ability to select PORT and HOST as connection options
-The ability to backdoor a directory of executables/dlls
-List all codecaves in the exe/dll
-Select the codecave in the exe/dll to backdoor, thereby not changing the filesize.
-Includes a simple XOR shellcode encoder.
![]()