Bpytop, bashtop python port is now available at https://github.com/aristocratos/bpytop
It's a lot faster and about a third as cpu heavy and has more features, including:
- Mouse support
- Toggleable mini mode
- More customization
- Graphs for memory consumption
Description
Resource monitor that shows usage and stats for processor, memory, disks, network and processes.
Features
- Easy to use, with a game inspired menu system.
- Fast and "mostly" responsive UI with UP, DOWN keys process selection.
- Function for showing detailed stats for selected process.
- Ability to filter processes.
- Easy switching between sorting options.
- Send SIGTERM, SIGKILL, SIGINT to selected process.
- UI menu for changing all config file options.
- Auto scaling graph for network usage.
- Shows message in menu if new version is available
- Shows current read and write speeds for disks
- Multiple data collection methods which can be switched if running on Linux
Themes
Bashtop now has theme support and a function to download missing local themes from repository.
See themes folder for available themes.
The builtin theme downloader places the default themes in
$HOME/.config/bashtop/themes. User created themes should be placed in $HOME/.config/bashtop/user_themes to be safe from overwrites.Let me know if you want to contribute with new themes.
Support and funding
Bug fixes and updates might be slow during normal workdays since I work full time as an industrial worker and don't have much time or energy left during the week. I'm looking into ways of funding this project that would allow me to take off time from my day job to work on this.
Any advice on how to get funding for open source projects is very welcome!
Update
You can now sponsor this project through github, see my sponsors page for options.
Also added donation links for paypal and ko-fi.
Any support is greatly appreciated!
Prerequisites
Mac Os X
Will not display correctly in the standard terminal! Recommended alternative iTerm2
Will also need to be run as superuser to display stats for processes not owned by user.
Linux, Mac Os X and FreeBSD
For correct display, a terminal with support for:
- 24-bit truecolor (See list of terminals with truecolor support)
- Wide characters (Are sometimes problematic in web-based terminals)
- Unicode Block “Braille Patterns” U+2800 - U+28FF
- Unicode Block “Geometric Shapes” U+25A0 - U+25FF
- Unicode Block "Box Drawing" and "Block Elements" U+2500 - U+259F
Notice
Dropbear seems to not be able to set correct locale. So if accessing bashtop over ssh, OpenSSH is recommended.
Dependencies
Linux, OSX and FreeBSD
bash (v4.4 or later) Script functionality will most probably break with earlier versions. Bash version 5 is highly recommended to make use of $EPOCHREALTIME variable instead of a lot of external date command calls.
GNU coreutils
GNU sed
Linux using /proc for data collection
GNU grep
ps from procps-ng (v3.1.15 or later)
GNU awk
OSX and FreeBSD or Linux using psutil for data collection
Python3 (v3.6 or later)
psutil python module (v5.7.0 or later)
Optionals for additional stats
(Optional OSX) osx-cpu-temp Needed to show CPU temperatures.
(Optional Linux) lm-sensors Needed to show CPU temperatures.
(Optional Linux) iostat (part of sysstat) Needed if you want disk read/write stats and are not using psutil data collection.
(Optional OSX/Linux/FreeBSD) curl (v7.16.2 or later) Needed if you want messages about updates and the ability to download themes.
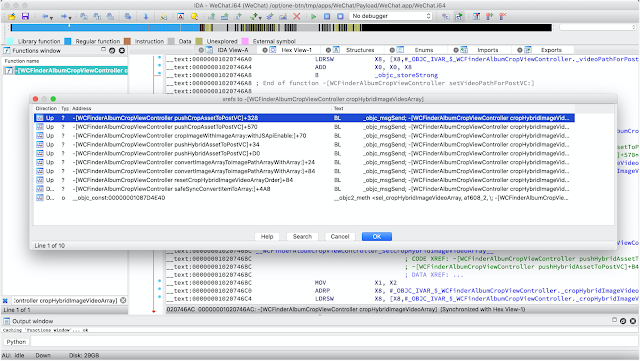
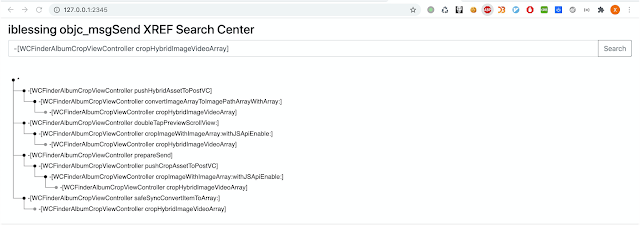
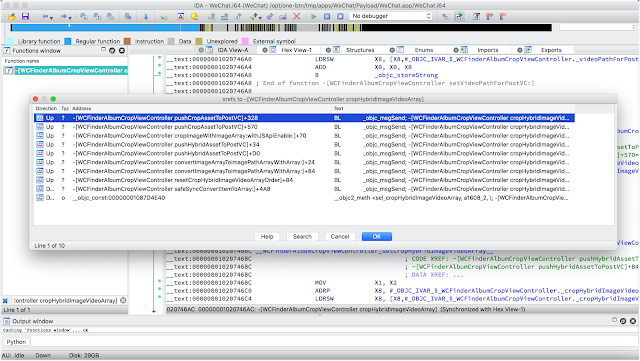
Screenshots
Main UI showing details for a selected process.
Main menu.
Options menu.
Installation
Dependencies installation OSX
Install homebrew if not already installed
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install.sh)"If you got python 3.6 or later installed outside of brew:
sudo python3 -m ensurepip
sudo python3 -m pip install psutilIf you haven't got python3 installed:
brew install python3
python3 -m pip install psutilInstall dependencies
brew install bash coreutils gnu-sed gitInstall optional dependency osx-cpu-temp
brew install osx-cpu-tempDependencies installation FreeBSD
Install with pkg and pip
sudo pkg install coreutils gsed git py37-psutilManual installation Linux, OSX and FreeBSD
Clone and install
git clone https://github.com/aristocratos/bashtop.git
cd bashtop
sudo make installto uninstall it
sudo make uninstallFreeBSD package
Available in FreeBSD ports
Install pre-built pacakge
sudo pkg install bashtopArch based
Available in the AUR as bashtop-git
Available in the Arch Linux repository as bashtop
Debian based
Available in official Debian repository since Debian 11
Available for debian/ubuntu from Azlux's repository
Or use quick installation:
Quick install go to DEB folder and type
sudo ./buildto uninstall it go to DEB folder and type
sudo ./build --removeGuix based
Available in official Guix repository since 6bbd0fd2
Installation
guix install bashtopUbuntu based
Available in official Ubuntu repository since Ubuntu 20.10
Available for Ubuntu from PPA repository
Add PPA repository and install bashtop
sudo add-apt-repository ppa:bashtop-monitor/bashtop
sudo apt update
sudo apt install bashtopFedora
Available in the Fedora repository.
Installation
sudo dnf install bashtopCentOS 8
Installation
dnf config-manager --set-enabled PowerTools
dnf install epel-release
dnf install bashtopRHEL 8
Installation
ARCH=$( /bin/arch )
subscription-manager repos --enable
"codeready-builder-for-rhel-8-${ARCH}-rpms"
dnf install epel-release
dnf install bashtopConfigurability
All options changeable from within UI. Config files stored in "$HOME/.config/bashtop" folder
bashtop.cfg: (auto generated if not found)
#? Config file for bashtop v. 0.9.21
#* Color theme, looks for a .theme file in "$HOME/.config/bashtop/themes" and "$HOME/.config/bashtop/user_themes"
#* Should be prefixed with either "themes/" or "user_themes/" depending on location, "Default" for builtin default theme
color_theme="Default"
#* Update time in milliseconds, increases automatically if set below internal loops processing time, recommended 2000 ms or above for better sample times for graphs
update_ms="2500"
#* Processes sorting, "pid" "program" "arguments" "threads" "user" "memory" "cpu lazy" "cpu responsive"
#* "cpu lazy" updates sorting over time, "cpu responsive" updates sorting directly
proc_sorting="cpu lazy"
#* Reverse sorting order, "true" or "false"
proc_reversed="false"
#* Show processes as a tree
proc_tree="false"
#* Check cpu temperature, only works if "sensors", "vcgencmd" or "osx-cpu-temp" commands is available
check_temp="true"
#* Draw a clock at top of screen, formatting according to strftime, empty string to disable
draw_clock="%X"
#* Update main ui when menus are showing, set this to false if the menus is flickering too much for comfort
background_update="true"
#* Custom cpu model name, empty string to disable
custom_cpu_name=""
#* Enable error logging to "$HOME/.config/bashtop/error.log", "true" or "false"
error_logging="true"
#* Show color gradient in process list, "true" or "false"
proc_gradient="true"
#* If process cpu usage should be of the core it's running on or usage of the total available cpu power
proc_per_core="false"
#* Optional filter for shown disks, should be names of mountpoints, "root" replaces "/", separate multiple values with space
disks_filter=""
#* Enable check for new version from github.com/aristocratos/bashtop at start
update_check="true"
#* Enable graphs with double the horizontal resolution, increases cpu usage
hires_graphs="false"
#* Enable the use of psutil python3 module for data collection, default on OSX
use_psutil="true"Command line options: (not yet implemented)
USAGE: bashtopTODO
Might finish off items out of order since I usually work on multiple at a time.
- Add options to change colors for text, graphs and meters.
- Fix cross platform compatibility for Mac OSX and *BSD: Working on OSX, and FreeBSD.
- Add support for showing AMD cpu temperatures.
- Add option to show tree view of processes.
- Add option to reset network download/upload totals.
- Add option to turn of gradient in processes list.
- Add gpu temp and usage. (If feasible)
- Add io stats for disks.
- Add cpu and mem stats for docker containers. (If feasible)
- Change process list to line scroll instead of page change.
- Add optional window for tailing log files.
- Add options for resizing all boxes.
- Add command line argument parsing.
- Builtin updater. Relevant PR #96 by Jukoo
- Add support for zram in memory box. Relevant PR #122 by perkinslr
- Miscellaneous optimizations and code cleanup.
- Add more commenting where it's sparse.
- Python port. (Porting started)