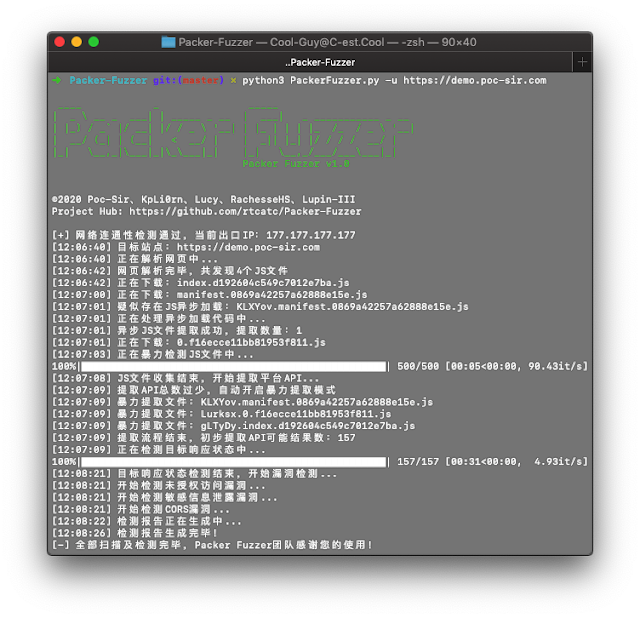
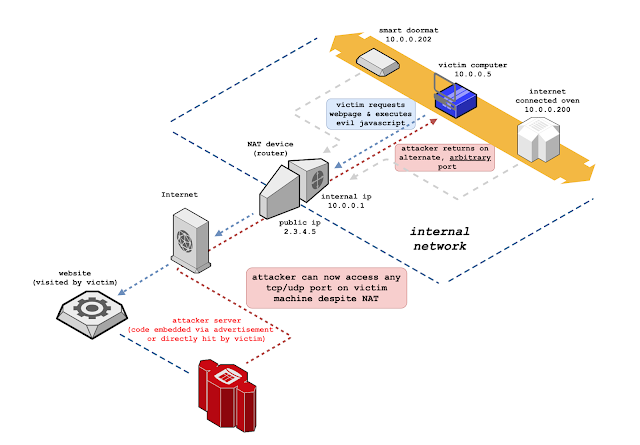
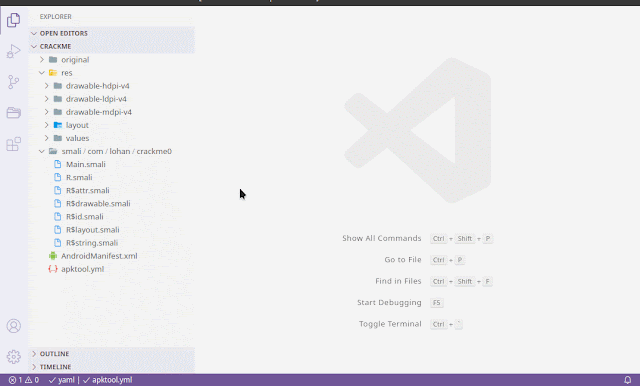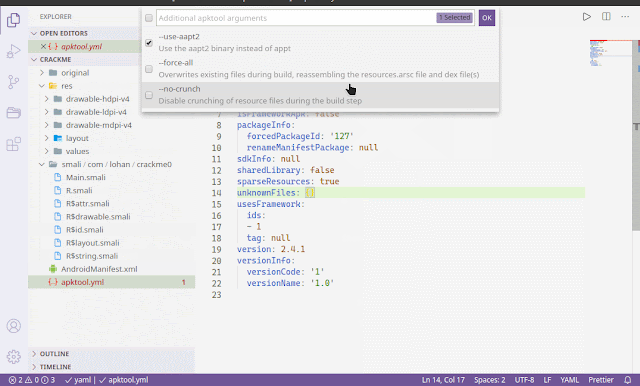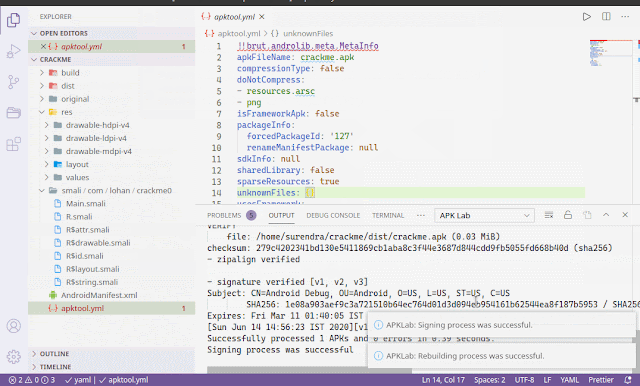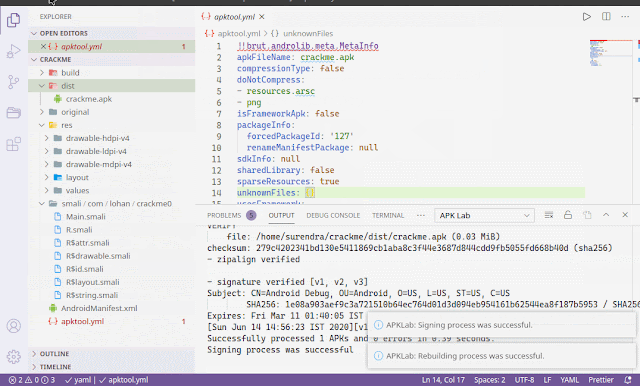
With the popularity of web front-end packaging tools, have you encountered more and more websites represented by Webpack packager in daily penetration testing and security services? This type of packager will package the API and API parameters of the entire site together for centralized Web call, which is also convenient for us to quickly discover the functions and API lists of the website, but often the number of JS files generated by these packagers is unusually large and total The amount of JS code is extremely large (more than ten thousand lines), which brings great inconvenience to our manual testing, and the Packer Fuzzer software came into being.
This tool supports automatic fuzzy extraction of the API corresponding to the target site and the parameter content corresponding to the API, and supports the fuzzing and efficient fuzzing of seven vulnerabilities: unauthorized access, sensitive information leakage, CORS, SQL injection, unauthorized access, weak password, and arbitrary file upload Rapid detection. After the scan is over, this tool also supports automatic generation of scan reports. You can choose the HTML version that is easy to analyze and the more formal doc, pdf, txt versions.
And you don’t have to worry about language problems caused by internationalization. This tool comes with five major language packages (including report templates): Simplified Chinese, French, Spanish, English, and Japanese (sorted according to translation accuracy). NoProfessional team translation.
Parameter introduction
You can use the python3 PackerFuzzer.py [options] command to run this tool. The content of options is as follows:
--h (--help)
Help command, no additional parameters, view all the parameters supported by this tool and their corresponding introduction;
--u (--url)
The URL path of the website to be scanned is a required option, for example: -u https://demo.poc-sir.com;
--c (--cookie)
Additional cookies content, can be empty, if filled in, it will be passed globally, for example: -c "POC=666;SIR=233";
--d (--head)
Additional HTTP header content, which can be empty, if filled in, it will be passed in globally, the default is Cache-Control:no-cache, for example: -d "Token:3VHJ32HF0";
--l (--lang)
Language option, when it is empty, the system will automatically select the corresponding language option, if there is no corresponding language pack, it will automatically switch to the English interface. The available language packs are: Simplified Chinese (zh), French (fr), Spanish (es), English (en), Japanese (ja), for example: -l zh;
--t (--type)
It is divided into basic version and advanced version. When it is empty, the basic version is used by default. The advanced version will rescan all APIs and fuzzy extract the corresponding parameters of the API, and perform: SQL injection vulnerabilities, horizontal unauthorized vulnerabilities, weak password vulnerabilities, and arbitrary file upload vulnerabilities. You can use the adv option to enter the advanced version, for example: -t adv;
--p (--proxy)
Global proxy, can be empty, if you fill in, use proxy IP globally, for example: -p https://hack.cool:8080;
--j (--js)
Additional JS file, can be empty, when you think there are other JS files that need to be analyzed by this tool, you can use this option, for example: -j https://demo.poc-sir.com/js/index.js, https://demo.poc-sir.com/js/vue.js;
--b (--base)
Specify the middle part of the API (for example, when an API is: https://demo.poc-sir.com/v1_api/login, its basedir is: v1_api), it can be empty, when you think the automatically extracted basedir of this tool is not accurate , You can use this option, for example: -b v1_api;
--r (--report)
Specify the report format to be generated. When it is empty, HTML and DOC format reports are generated by default. Available report formats are: html, doc, pdf, txt, for example: -r html,pdf;
--e (--ext)
Whether to enable the extension plug-in option, this tool supports users to self-write plug-ins and save them in the ext directory (for how to write, please refer to the demo.py file in the corresponding directory). The default is off. When the user uses the on command to open, the tool will automatically execute the plug-ins in the corresponding directory, for example: -e on;
--f (--flag)
The SSL connection security option, when it is empty, is closed by default. In this state, all insecure connections will be blocked. If you want to ignore the SSL security status, you can use the 1 command to enable it, and all certificate errors will be ignored, for example: -f 1;
-s (--silent)
The Silent option, once enabled, all operations that ask for YES or NO will automatically be set to YES, and the content after the parameter is the name of the scan report (custom report name), which can be used for unattended, batch operations, plug-in calls, for example: -s Scan_Task_777.
![]()