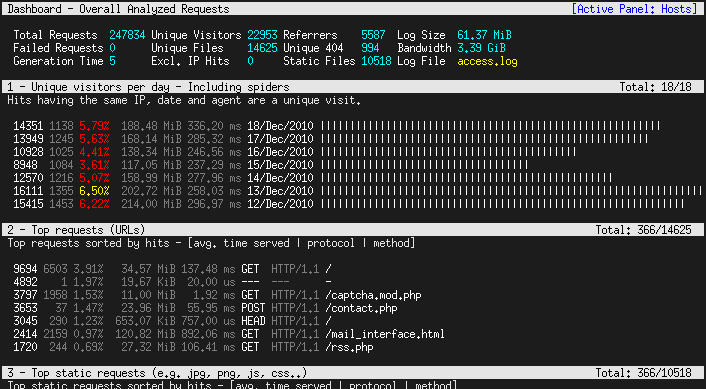
AutoReaver is bash script which provides multiple access point attack using reaver and BSSIDs list from a text file.
If processed AP reaches rate limit, script goes to another from the list, and so forth.
HOW IT WORKS ?
Script takes AP targets list from text file in following format
REQUIREMENTS
USAGE EXAMPLE
First you have to download lastest version
ADDITIONAL FEATURES
You can define channel as random by setting it's value (in myAPTargets file) to R, you can force script to automatically find AP channel.
Example:
But remember that you probably should also increase value of
![]()
If processed AP reaches rate limit, script goes to another from the list, and so forth.
HOW IT WORKS ?
Script takes AP targets list from text file in following format
BSSID CHANNEL ESSID
AA:BB:CC:DD:EE:FF 1 MyWlan
00:BB:CC:DD:EE:FF 13 TpLink
00:22:33:DD:EE:FF 13 MyHomeSSID
- Every line of list file is checked separately in for loop
- After every AP on the list once, script automatically changes MAC address of your card to random MAC using macchanger (you can also setup your own MAC if you need),
- Whole list is checked again and again, in endless while loop, until there is nothing to check loop is stopped,
- Found PINS/WPA PASSPHRASES are stored in {CRACKED_LIST_FILE_PATH} file.
REQUIREMENTS
- Wireless adapter which supports injection (see [https://code.google.com/p/reaver-wps/wiki/SupportedWirelessDrivers Reaver Wiki])
- Linux Backtrack 5
- Root access on your system (otherwise some things may not work)
- AND if you use other Linux distribution*
- Reaver 1.4 (I didn't try it with previous versions)
- KDE (unless you'll change 'konsole' invocations to 'screen', 'gnome-terminal' or something like that... this is easy)
- Gawk (Gnu AWK)
- Macchanger
- Airmon-ng, Airodump-ng, Aireplay-ng
- Wash (WPS Service Scanner)
- Perl
USAGE EXAMPLE
First you have to download lastest version
git clone https://code.google.com/p/auto-reaver/cd ./auto-reaverchmod 700 ./washAutoReaver
chmod 700 ./autoReaver./washAutoReaverList > myAPTargetscat ./myAPTargets./autoReaver myAPTargetsADDITIONAL FEATURES
- Script logs dates of PIN attempts, so you can check how often AP is locked and for how long. Default directory for those logs is ReaverLastPinDates.
- Script logs each AP rate limit for every AP (default directory is /tmp/APLimitBSSID), so you can easily check when last rate limit occured
- You can setup your attack using variables from configurationSettings file (sleep/wait times between AP`s and loops, etc.)
- You can disable checking AP by adding "#" sign in the beginning of line, in myAPTargets file (then AP will be ommited in loop)
- (added 2014-07-03) You can setup specific settings per access point.
To do that for AP with MAC AA:BB:CC:DD:EE:FF, just create file ./configurationSettingsPerAp/AABBCCDDEEFF
and put there variables from ./configurationSettings file that you want to change for example:ADDITIONAL_OPTIONS="-g 10 -E -S -N -T 1 -t 15 -d 0 -x 3";
You can define channel as random by setting it's value (in myAPTargets file) to R, you can force script to automatically find AP channel.
Example:
AA:BB:CC:DD:EE:FF R MyWlanBut remember that you probably should also increase value of
BSSID_ONLINE_TIMEOUT variable - since hopping between all channels takes much more time than searching on one channel.